Things to Know to Get Hired as a Turing Engineer
If you’re reading this, you’re likely a software developer who is considering applying for Turing.com. You might have just learned about Turing a few minutes ago, or you might have already gotten past the teaser coding problem on Turing’s landing page, created a profile, and are now staring at an extensive list of Turing tests. Either way, you (most likely a high-achieving and high-aspiring software developer) are on the right track. The number of high-profile silicon valley companies that hire remote software developers through Turing is increasing each week, and more than 160,000 software developers have signed up for Turing in its first year alone. You’re smart to be jumping on this opportunity now! But, if you’re like most developers, some part of you is likely starting to wonder if you’re sufficiently prepared to dive into the application.
Even the most seasoned software developers can get anxious in the days or hours leading up to a technical interview. So, to help you out, we’ve reached out to some Turing engineers who passed Turing’s tests with exceptionally high marks and are now enjoying a remote software job with top US companies. We asked them to share what they think is most important for a software engineer to know or do before applying to Turing. We even asked the primary designer of the Turing Tests himself, Turing’s VP of Engineering, Zan Doan, (previously an Engineering Manager at Facebook) to give his thoughts. Here is what they said:
-
Sharpen your problem-solving skills
First and foremost, as in any Silicon Valley technical interview process, Turing engineers are expected to be expert problem solvers, able to manipulate data structures and common algorithms to solve a variety of problems while optimizing for speed and efficiency. Everaldo, a Turing engineer based in Curitiba, Brasil, gave the following advice:
“Turing applicants should familiarize themselves with sites like HackerRank and Codewars, where they can sharpen their problem-solving skills. They should also study dynamic programming and Big O notation to understand techniques for coding challenges, since, if you implement a naive solution, it will get a lower score or might timeout if the solution is quadratic or exponential.”
Everaldo also recommended studying the well-known book “Cracking the Coding Interview” by Gayle McDowell. Not a bad idea considering one can always count on seeing a few Stanford CS students crouched over that “little green CS bible” in the Stanford dining halls during the interview season. Mastering the material there will put you in a position to get the same caliber jobs that many of those same Stanford students are pursuing! -
Know your tech stacks
One thing that is relatively unique about Turing’s tests is that you have the opportunity to demonstrate mastery in an array of tech stacks with which you’re familiar. Whether you’re a Swift iOS developer, a MongoDB + React + Node.js full-stack developer, a Frontend developer with expertise in Flutter, a Python developer capable of scaling a Django backend, or anything else, you can find corresponding tests on Turing’s platform. Dhyey, a Turing engineer based in Ahmedabad, India, says, “Make sure to take and pass as many tech stack tests as possible. Proving you have a range of skills will make you eligible for multiple roles and increase your chances of getting hired.”
Doing well on these specific tech stack tests might require a little review before you jump into them. Zech, a Turing engineer, based in Addis Ababa, Ethiopia, recommends you do the following:“Take a little time to lightly review anything about that particular technology or language you’re not very familiar with because the tests tend to assess your knowledge about it from end to end. Of course, this doesn’t mean you should dive into a full-on ‘study for exam mode’ but just refresh your knowledge of a few things. If you’ve used a language/technology professionally for some time, you should pass the test without much problem.”
-
Showcase your technical experience
Investing time into filling out all the details of your profile and past experiences may be a hassle, but it will give you an edge over other vetted candidates. Dhyey emphasizes this point saying, “since the process is highly competitive and there is very little human interaction, it is very crucial for your profile to accurately reflect your ability for you to get picked over other vetted candidates.”
If that alone doesn’t convince you of the importance of highlighting your past accomplishments, projects, and experiences, this is the area that Zan Doan, the primary designer of the Turing Tests, also believes is most important. He says:“The word I would use to describe the best Turing developers is ‘hands-on.’ Turing jobs often require developers to adapt to a startup environment and make an impact quickly. Because of this, Turing tests not only ask the candidates questions about their general work experience but also hands-on questions about detailed implementations.”
Showcasing your ability to excel in a hands-on environment by taking care to describe your past technical experiences in your profile accurately will prime you for success on Turing.
-
Finally, prepare your workspace for success.
The Turing application process is similar to any technical interview, with the added caveat that the online tests (and later on, the possible interview) are all done remotely, meaning you’re in charge of preparing your space.
On this point, Zech recommends, “make sure you’re in a relaxed environment with little to no distractions. You’ll need to have a working and stable internet connection, especially since you can’t retake an exam within three months in the event you fail.
Similarly, if you qualify for an interview, Everaldo says, “it’s just like a regular interview: be ready, on time, dress code, be polite, and don’t be afraid to ask questions. Also, it helps to have a good setup for the interview. Have a strong Internet connection, headset, mic, and test the setup before the meeting.
And that’s about it! If you feel well-enough prepared in the above four areas, you should have no problem feeling confident clicking “start” to begin taking Turing’s tests or signing into a remote Turing interview. Silicon Valley opportunities are at your doorstep. The most beautiful thing about Turing’s application process is its hyper-focus on finding talent. We believe talent can be found anywhere and can be of all races and genders. And if, by chance, you’re not successful in your first shot at applying to Turing, a computer science education has become so democratized that we’re confident you can study up, come back, and succeed another day. Remember, at Turing, we know that not only is talent universal, but opportunity as well.
Ready to get started? Apply to Turing’s remote software developer jobs now.
Join a network of the world's best developers and get long-term remote software jobs with better compensation and career growth.


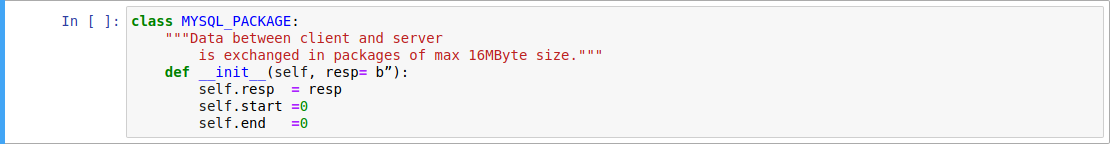
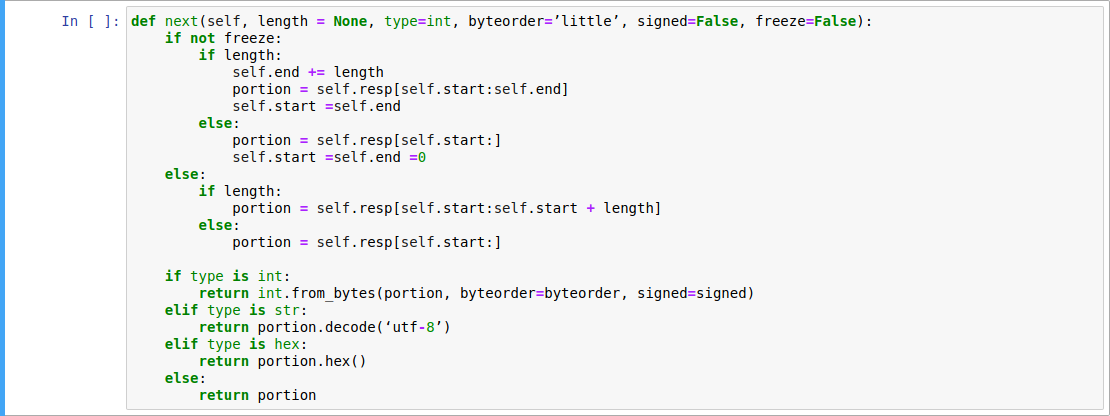
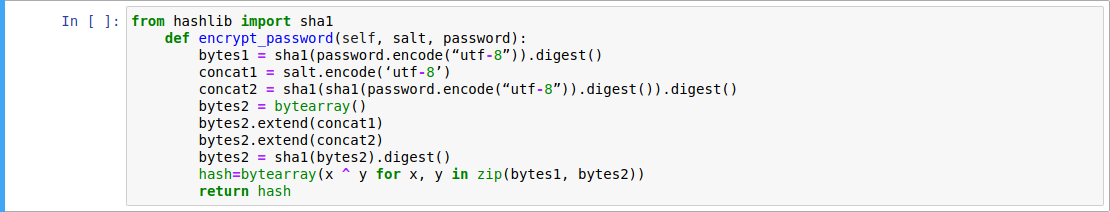







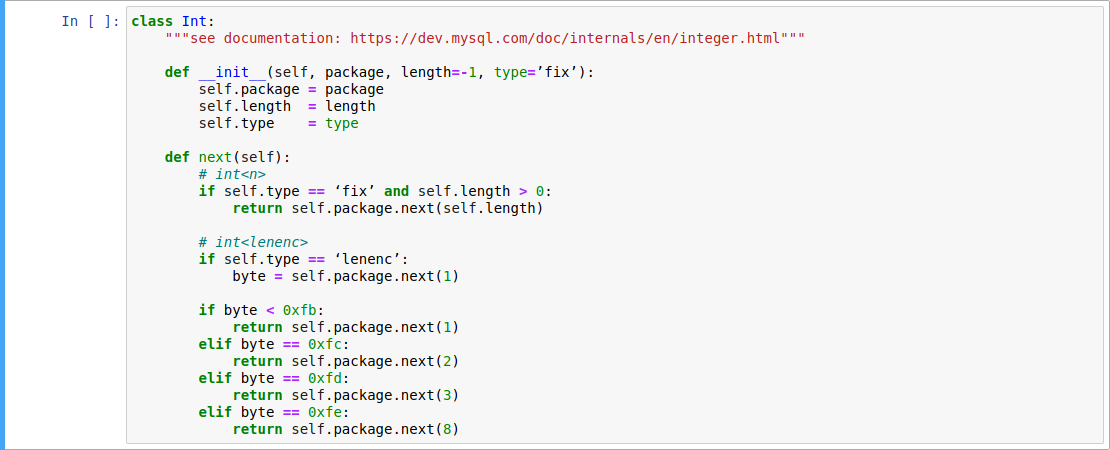
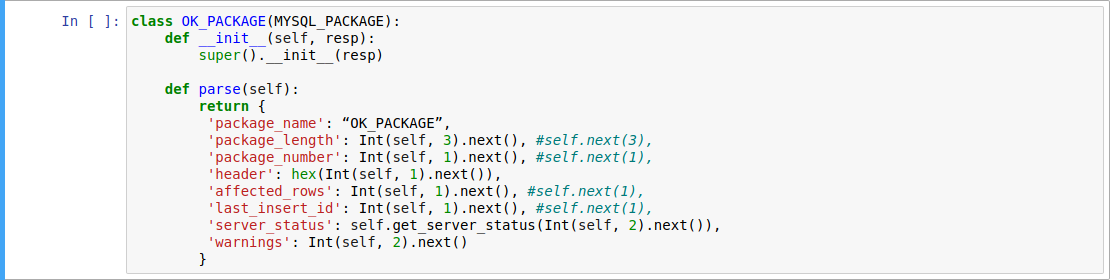
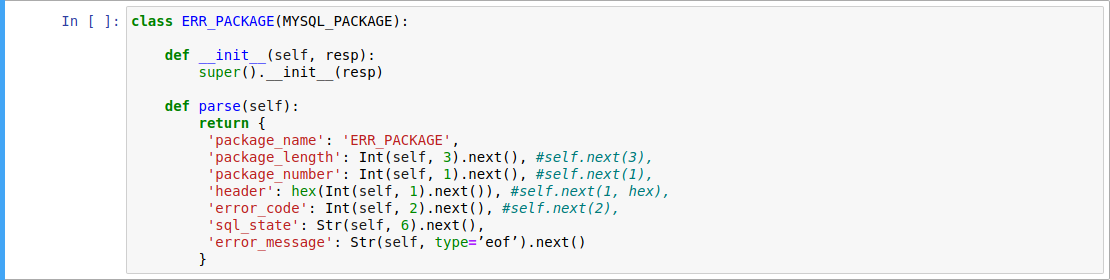
 OK package and ERR package are the response package of server after authentication or after sending query to server on command phase.
OK package and ERR package are the response package of server after authentication or after sending query to server on command phase.