Leverage Turing Intelligence capabilities to integrate AI into your operations, enhance automation, and optimize cloud migration for scalable impact.
Advance foundation model research and improve LLM reasoning, coding, and multimodal capabilities with Turing AGI Advancement.
Access a global network of elite AI professionals through Turing Jobs—vetted experts ready to accelerate your AI initiatives.
FOR DEVELOPERS
Master React User Authentication: A Comprehensive Guide
User authentication stands as the cornerstone of modern digital security, forming an essential line of defense against unauthorized access and safeguarding user data. In the realm of React applications, understanding the imperative role of user authentication is paramount to crafting a secure and trustworthy environment for users.
Table of Contents
- 1. Introduction to User Authentication in React
- 1.1. The Imperative Role of User Authentication
- 1.2. Understanding the React Framework and its Authentication Challenges
- 2. Fundamentals of Authentication
- 2.1. Unveiling the Distinction between Authentication and Authorization
- 2.2. An In-Depth Exploration of Common Security Threats
- 2.3. Deeper Dive into JSON Web Tokens (JWT) and their Mechanisms
- 3. Setting Up React App and User Authentication
- 3.1. A Step-by-Step Guide to Initializing a React App
- 3.2. Harnessing the Power of React Router for Seamless Navigation
- 3.3. Crafting Robust User Registration and Login Forms
- 3.4. Harnessing the Flexibility of React Context for Advanced State Management
- 4. Backend Integration
- 4.1. Critical Decisions: Choosing the Right Backend Technologies
- 4.2. Blueprint for Developing RESTful APIs Dedicated to User Management
- 4.3. Elevating Security: Comprehensive Methods for Storing User Passwords
- 4.4. Token Management Strategies: Ensuring Consistent Security on the Server
- 4.5. Exploring Additional Security Layers: Two-Factor Authentication
- 5. Frontend Authentication Workflow
- 5.1. Safeguarding Routes: Design Principles for Protected Routes
- 5.2. Building User Sessions: A Deep Dive into Token-Based Mechanisms
- 5.3. Providing a Graceful Exit: The Logout Functionality Unveiled
- 6. Best Practices for User Authentication in React
- 6.1. The Ever-Evolving Landscape: Importance of Keeping Dependencies Updated
- 7. Conclusion
Introduction to User Authentication in React
The Imperative Role of User Authentication
Authentication, essentially, verifies users' identities before granting them access to specific resources or functionalities. While authorization determines the actions authenticated users can perform, authentication ensures that only legitimate users gain entry. In the context of React applications, where sensitive data and interactions occur, robust authentication mechanisms provide the fundamental shield against data breaches and privacy violations.
The user's authentication journey often begins with inputting credentials, such as usernames and passwords. These credentials securely transmit to the backend, where they undergo validation. One of the most prevalent techniques for authentication is using JSON Web Tokens (JWTs). JWTs offer a secure and compact means of transmitting user information between the client and server. This technology not only improves the overall user experience by reducing the need for constant re-authentication but also enhances security by incorporating digital signatures to validate token authenticity.
In React applications, we witness the imperative role of user authentication in every step of the user's interaction. From granting access to specific routes and functionalities to controlling the visibility of personalized content, authentication shapes the overall user experience, determining an application's success. A properly implemented authentication system not only safeguards sensitive data but also fosters trust among users, positioning an application as a reliable platform worthy of engagement.
As we delve deeper into the layers of user authentication in React applications, we see that this process extends far beyond a mere gatekeeper. It acts as a guardian of data integrity, a facilitator of seamless user experiences, and an embodiment of the commitment to user privacy. Through a nuanced understanding of its imperative role, developers can navigate the complexities of authentication to build applications that prioritize both security and user satisfaction.
Understanding the React Framework and its Authentication Challenges
The React framework has revolutionized web development by offering a declarative and component-based approach to building user interfaces. However, its unique architecture also presents distinct challenges when implementing robust user authentication systems.
React's component-driven nature encourages the development of reusable and modular UI elements. While this design philosophy streamlines creating complex interfaces, it also introduces complexities in managing user authentication. Authentication-related components must seamlessly integrate with the overall application structure while ensuring airtight security. This demands a thoughtful balance between the simplicity of component composition and the intricacies of data protection.
Moreover, React's single-page application (SPA) paradigm presents challenges for authentication. SPAs load a single HTML page and dynamically update content as users interact, providing a fluid and engaging user experience. However, this also means that security measures must be diligently applied to prevent unauthorized access to different parts of the application, as traditional server-side rendering is not in play.
State management in React adds another layer of consideration. React's state management tools like Redux or Context API are powerful for maintaining global state, but handling authentication states—such as logged-in or logged-out—requires careful orchestration to ensure consistency across components and routes. Meticulous synchronization becomes essential to guarantee that authenticated states appropriately propagate throughout the application.
Furthermore, React applications often communicate with backend servers via APIs. This introduces the challenge of securely transmitting and storing sensitive user data, such as authentication tokens. The risk of cross-site scripting (XSS) attacks, where malicious scripts are injected into web pages, calls for rigorous input validation and output sanitization strategies.
As we navigate the realm of user authentication within the React framework, it's crucial to recognize that the challenges presented by this innovative technology are not insurmountable barriers. Instead, they inspire developers to design ingenious solutions that align with React's philosophy of efficiency and modularity while upholding the utmost security standards. By delving into these challenges, we unearth opportunities to enhance our understanding of React's intricacies and to craft authentication systems that seamlessly blend innovation with protection.
Fundamentals of Authentication
Unveiling the Distinction between Authentication and Authorization
In the realm of digital security, the terms "authentication" and "authorization" often intertwine, yet they play distinct and pivotal roles within the user access landscape. Understanding this fundamental differentiation is paramount for building secure and efficient React applications.
Authentication, the first line of defense, revolves around establishing the identity of users. It involves the process of verifying user-supplied credentials, such as usernames and passwords. Through techniques like token-based authentication or session-based authentication, the system ensures that only legitimate users gain access to protected resources. By confirming the user's identity, authentication serves as the gateway to the application, determining who is allowed to interact with it.
Authorization comes into play after authentication. Once a user's identity is verified, authorization defines what actions and resources that user is permitted to access. It involves the configuration of user roles, permissions, and access levels, ensuring that users can only interact with parts of the application that align with the designated roles. For instance, while a regular user may be authorized to view content, an administrator could have the authority to modify or delete it. Authorization serves as the gatekeeper that governs the extent of user interactions within the application.
React applications, with their component-based structure, demand a clear grasp of this distinction. While authentication verifies the user's identity and initiates their interaction journey, authorization molds the flow of that interaction, dictating what functionalities they can engage with. Blurring these lines can lead to security vulnerabilities or inadequate user experiences.
A practical understanding of these concepts becomes vital when designing user flows and implementing role-based access controls. As developers, comprehending the intricate interplay between authentication and authorization empowers us to construct applications that not only guard sensitive data but also provide users with tailored and meaningful experiences. By unveiling and respecting the distinction between these two pillars of access management, we establish a solid foundation upon which secure and user-centric React applications can thrive.
An In-Depth Exploration of Common Security Threats
In the intricate landscape of web application development, a comprehensive understanding of common security threats is indispensable to fortifying React applications against potential vulnerabilities. This exploration delves into some prevalent security threats, shedding light on their implications and preventive measures.
- Cross-Site Scripting (XSS): XSS attacks involve injecting malicious scripts into web pages viewed by other users. This can lead to unauthorized data exposure, hijacked sessions, and even malware distribution. Preventive measures include input validation, output encoding, and the use of Content Security Policy (CSP) headers to restrict script execution.
- Cross-Site Request Forgery (CSRF): CSRF attacks exploit the trust that a user has in a particular website by tricking them into performing actions they didn't intend. These attacks can result in unauthorized actions being executed on behalf of the user. Prevention involves implementing anti-CSRF tokens and enforcing same-origin policy.
- SQL Injection: Inadequately sanitized user inputs can enable attackers to manipulate SQL queries, potentially gaining unauthorized access to the database. Safeguarding against SQL injection entails using parameterized queries or prepared statements to prevent malicious input from impacting query execution.
- Security Misconfigurations: Improperly configured security settings can lead to data exposure or unauthorized access. Regular security audits and adherence to best practices can mitigate the risks associated with misconfigurations.
- Insecure Deserialization: Attackers exploit vulnerabilities in the deserialization process to execute arbitrary code or gain unauthorized access. Developers can mitigate this threat by employing proper input validation, whitelisting, and monitoring deserialization activities.
- Sensitive Data Exposure: Inadequate encryption or improper handling of sensitive data can lead to data breaches. Ensuring data encryption, the utilization of secure communication protocols (HTTPS), and adherence to data protection regulations are crucial.
- Broken Authentication: Weak authentication mechanisms or improperly managed sessions can lead to unauthorized access. Robust password policies, multi-factor authentication, and proper session management can counter this threat.
- Insecure Dependencies: Using outdated or vulnerable dependencies can open doors for attackers. Regularly updating dependencies, monitoring for security patches, and employing dependency scanning tools are essential practices.
- Insufficient Logging and Monitoring: Without proper logging and monitoring, detecting and responding to security incidents becomes challenging. Implementing comprehensive logging and setting up real-time monitoring can aid in identifying and mitigating potential breaches.
- Phishing and Social Engineering: Human vulnerabilities can be exploited through phishing attacks, tricking users into revealing sensitive information. Regular user education, spam filters, and multi-factor authentication can bolster defenses against such threats.
By delving into these common security threats and embracing proactive measures, React developers can lay the groundwork for creating applications that not only provide exceptional user experiences but also uphold the highest standards of data protection and integrity.
Deeper Dive into JSON Web Tokens (JWT) and their Mechanisms
JSON Web Tokens (JWTs) have emerged as a versatile and secure method for transmitting information between parties, commonly used for authentication and data sharing in web applications. This deeper exploration into JWTs unravels their inner mechanisms and sheds light on their significance in React application security.
At its core, a JWT is a compact and self-contained data structure that consists of three parts: header, payload, and signature. The header typically contains information about the token's type (JWT) and the signing algorithm used. The payload stores claims or statements about the user, including user ID, roles, and expiration time. The signature ensures the token's integrity and authenticity, preventing unauthorized tampering.
JWTs operate on the principle of stateless authentication. Once a user is authenticated and a JWT is issued, subsequent requests include this token. This eliminates the need for servers to store session data, promoting scalability and simplifying token validation. This statelessness aligns well with React's architecture, allowing for efficient development of single-page applications.
One of JWT's key advantages lies in its support for token-based authentication. When a user logs in, a JWT is generated and sent to the client. This token is then included in the headers of subsequent requests, allowing the server to identify and validate the user without repeatedly checking credentials or sessions. This not only enhances security but also improves the overall user experience by reducing unnecessary re-authentication.
JWTs can also store custom claims, offering developers the flexibility to include additional user-related data. However, it's important to exercise caution when including sensitive information in the payload, as the payload is base64-encoded and easily deciphered by anyone who has the token. Confidential information should be stored in the server's database and only referenced via a unique identifier in the payload.
To implement JWTs effectively, developers need to select a robust signing algorithm (such as HMAC, RSA, or ECDSA) based on the security requirements of their application. Libraries like 'JSON web token' for Node.js simplify JWT creation, verification, and decoding.
While JWTs offer numerous advantages, they are not without potential pitfalls. Care must be taken to set appropriate token expiration times, implement secure token storage (e.g., HTTP-only cookies), and guard against vulnerabilities like XSS attacks that could compromise tokens.
In React applications, understanding the mechanisms of JWTs empowers developers to design efficient and secure authentication systems. By harnessing JWTs' stateless nature and cryptographic features, developers can build React applications that provide a seamless user experience while maintaining strong security protocols.
Setting Up React App and User Authentication
A Step-by-Step Guide to Initializing a React App
Initializing a React application serves as the foundational step toward building secure and efficient user authentication systems. By following this step-by-step guide, developers can lay the groundwork for crafting React applications that adhere to best practices and security standards.
1. Install Node.js and npm: Ensure Node.js and npm (Node Package Manager) are installed on your system. These tools are essential for managing dependencies and running JavaScript applications.
2. Create a New React App: Open your terminal and execute the following command to create a new React app named "my-auth-app":

This command initializes a new React project with all the necessary files and configurations.
3. Navigate to the App Directory: Move into the app directory using the following command:

4. Start the Development Server: Launch the development server to preview your React app in the browser:

This command starts the development server and opens your app in your default browser.
5. Folder Structure Overview: Familiarize yourself with the app's folder structure. Key directories include:-

6. Create Components: Begin building your React app by creating components. Components are the building blocks of your app's UI. For instance, you could create components for login forms, registration forms, and user dashboards.

7. Implement Routing: React Router simplifies navigation in your app. Install it using:

Create routes for different parts of your application.

8. State Management: Depending on your preference, you can implement state management using tools like Redux or React Context API. This facilitates managing user authentication states.
Harnessing the Power of React Router for Seamless Navigation
In the realm of React application development, effective navigation plays a pivotal role in providing users with intuitive and seamless interactions. React Router emerges as a powerful solution to tackle navigation challenges, offering a declarative and component-based approach that aligns perfectly with React's philosophy.
React Router, a widely adopted library, simplifies the process of managing navigation within single-page applications. It enables developers to create dynamic, client-side routes that mirror traditional multi-page applications without the need for full-page refreshes. This not only enhances the user experience by eliminating the waiting time associated with page loads but also optimizes performance.
By leveraging the <BrowserRouter> component from React Router, developers can encapsulate the entire application and define routes within it. Each route corresponds to a particular component or view, allowing for smooth navigation between different parts of the application. This component-based routing approach aligns seamlessly with React's architecture, making it intuitive to incorporate routing within the overall app structure.
Nested routes further enhance React Router's flexibility. Developers can nest routes within components, enabling a hierarchical navigation structure that mirrors the application's content hierarchy. This proves particularly useful in scenarios like user dashboards, where different sections require distinct routes.
React Router also facilitates parameterized routes, enabling dynamic content rendering based on URL parameters. This is valuable for scenarios like user profiles or product details, where a single component can be reused for multiple instances.
Furthermore, React Router provides support for route guarding, an essential feature for user authentication. Protected routes can be created by wrapping components within the <Route> element and implementing authorization checks. This ensures that only authenticated users can access certain parts of the application, bolstering security.
Incorporating React Router into your application is straightforward:

By embracing React Router, developers can create seamless and dynamic navigation experiences within React applications. This not only enhances user engagement but also aligns to craft applications that seamlessly blend modern web development paradigms with efficient navigation systems.
Crafting Robust User Registration and Login Forms
User registration and login forms are the gateway to a secure and personalized user experience in React applications. Crafting these forms with a focus on robustness and security is crucial to ensuring the integrity of user data and authentication processes.
- User Registration Form: When designing the user registration form, developers should prioritize collecting necessary information while minimizing user friction. Fields like username, email, and password should be included, and password requirements should be communicated clearly. Utilizing form validation libraries, such as formik or react-hook-form, ensures that user inputs are accurate and properly formatted.

- User Login Form: The user login form should enable users to securely authenticate themselves. It typically consists of fields for email/username and password. Implementing secure password handling, including hashing and salting on the server side is paramount. Frontend validation can be supplemented by backend validation to prevent unauthorized access.

By adopting best practices such as input validation, secure password handling, and frontend-backend synchronization, developers can ensure the robustness and security of user registration and login forms. These forms lay the groundwork for a secure authentication process that underpins the user's experience within the React application.
Harnessing the Flexibility of React Context for Advanced State Management
React Context is a powerful tool for managing global states in React applications. Leveraging its flexibility, developers can efficiently handle authentication states and user data across the entire application, ensuring a consistent and secure user experience.
- Creating an Authentication Context: To manage authentication states, start by creating an Authentication Context. This context can include information such as the user's ID, authentication status, and any relevant user data. Here's a simplified example:

- Consuming the AuthContext: Consuming the Authentication Context is straightforward. Wrap your entire application with the AuthProvider and use the useAuth hook in any component that needs access to authentication data.

- Securing Routes with Context: With React Context, securing routes based on authentication status becomes seamless. Wrap components that require authentication with a check using the useAuth hook:

By harnessing React Context for advanced state management, developers can seamlessly propagate authentication states and user data throughout the application. This not only simplifies state management but also enhances security and ensures a consistent user experience across all components and routes.
Backend Integration
Critical Decisions: Choosing the Right Backend Technologies
Selecting the appropriate backend technologies is a pivotal decision when building a secure and efficient React application with user authentication. The backend serves as the foundation for user data storage, authentication logic, and API interactions. Here are some critical considerations when making this choice:
- Language and Framework: The choice of programming language and backend framework significantly impacts your application's scalability, performance, and maintainability. Python, Node.js, Ruby on Rails, Django, and Express.js are among the popular options. Your choice should align with your development team's expertise and the specific requirements of your project.
- Database Management: The database technology you select affects data storage and retrieval. SQL databases like PostgreSQL and MySQL offer strong data integrity and relational modeling capabilities, making them suitable for complex data structures. NoSQL databases like MongoDB excel in handling large volumes of unstructured data, providing flexibility for certain use cases.
- Authentication Libraries: The backend should integrate with authentication libraries or frameworks that simplify user authentication and session management. For instance, libraries like Passport.js (for Node.js) provide robust authentication solutions with various authentication strategies.
- API Design: Designing a well-structured API is crucial for smooth communication between the front end and back end. Implement RESTful or GraphQL APIs depending on your project's requirements. Ensure that API endpoints are protected, and sensitive data is transmitted securely.
- Security Considerations: Security should be a top priority. Implement React security best practices such as input validation, output encoding, and protecting against common vulnerabilities like SQL injection, XSS, and CSRF attacks. Utilize HTTPS for secure data transmission and consider security headers like Content Security Policy (CSP).
- Scalability and Performance: The backend technology stack should be able to scale horizontally to accommodate increased traffic. Employ load balancing and caching mechanisms when necessary. Monitor application performance and optimize database queries and API responses.
- Compliance and Regulations: If your application deals with sensitive user data, ensure that your backend technologies comply with data protection regulations like GDPR or HIPAA. Implement encryption and data anonymization as required.
Choosing the right backend technologies sets the stage for a secure and efficient user authentication system in your React application. Evaluate these factors carefully, as they play a crucial role in determining the application's reliability, scalability, and overall success.
Blueprint for Developing RESTful APIs Dedicated to User Management
Building robust and secure RESTful APIs dedicated to user management is a crucial step in developing a React application with strong authentication capabilities. This blueprint outlines key considerations and steps for creating a user-centric API.
- API Endpoints Design: Begin by defining the API endpoints that will handle user-related operations, including registration, login, profile retrieval, and updates. Use RESTful conventions to structure these endpoints logically, making them intuitive for developers and clients.

- Authentication and Authorization: Implement robust authentication mechanisms to secure user data and operations. Consider using JWT (JSON Web Tokens) for token-based authentication. Ensure that API endpoints requiring authentication are protected and can only be accessed by authenticated users.
- User Validation: Input validation is paramount to prevent security vulnerabilities. Validate user inputs on the server side to prevent common issues like SQL injection and XSS attacks. Libraries like Express Validator for Node.js can simplify this process.
- User Registration: Create an endpoint for user registration. Validate and sanitize user-provided data before storing it in the database. Employ secure password hashing and salting techniques to store passwords.
- User Login: Implement a login endpoint that verifies user credentials against the stored data. Generate and return a JWT upon successful authentication. Handle password reset and recovery mechanisms securely, including email validation and password reset tokens.
- User Profile Management: Enable users to update their profiles. Implement an endpoint for profile retrieval and updates. Secure these endpoints to ensure that users can only access and modify their profiles.
- User Deletion: Create an endpoint for user account deletion. Implement checks to ensure that only authorized users can request account deletion and confirm user identity before proceeding.
- Logging and Monitoring: Implement logging to record API activity, errors, and security-related events. Set up monitoring tools to detect and respond to anomalies or suspicious behavior promptly.
- Error Handling: Develop consistent error-handling mechanisms for the API. Provide informative error messages while avoiding leaking sensitive information to clients.
- Testing and Documentation: Thoroughly test each API endpoint to ensure correctness and security. Document the API endpoints, their expected inputs, responses, and error codes for both internal and external developers.
By following this blueprint and adhering to best practices, you can construct a reliable and secure set of RESTful APIs dedicated to user management. These APIs will serve as the backbone of your React application's authentication system, enabling smooth and secure user interactions.
Elevating Security: Comprehensive Methods for Storing User Passwords
The security of user passwords is a critical aspect of any authentication system in a React application. Employing robust methods for storing user passwords is paramount to safeguarding sensitive user data. Here are comprehensive approaches for enhancing password security:
- Hashing and Salting: Hashing is the process of converting a plaintext password into a fixed-length string of characters, which is nearly impossible to reverse. Salt, a random value unique to each user, is added before hashing. This adds an extra layer of security, as even identical passwords will have different hash values due to the unique salt.

- Use a Strong Hashing Algorithm: Choose a strong and widely recognized hashing algorithm such as bcrypt or Argon2. These algorithms are designed to be computationally expensive, making it extremely difficult for attackers to perform brute force or dictionary attacks.
- Iterative Hashing: Perform multiple iterations of hashing. This slows down attackers attempting to guess passwords by increasing the time required to hash each password.

- Store Salt and Hash Together: Ensure that the salt used for hashing is stored alongside the hashed password in the database. This allows you to verify passwords during authentication.
- Implement Password Policies: Enforce password policies that require users to create strong passwords. This includes minimum length requirements, the use of special characters, and regular password expiration.
- Secure Password Recovery: When allowing users to reset forgotten passwords, use secure methods such as sending password reset tokens via email. Ensure that these tokens have a short lifespan and can only be used once.
- Monitor for Data Breaches: Regularly monitor data breaches and leaks. If any password hashes are compromised, prompt users to change their passwords immediately.
- Educate Users: Educate users about password security best practices, such as not reusing passwords across different websites and using password managers.
- Two-Factor Authentication (2FA): Implement 2FA to provide an additional layer of security. This requires users to provide a second form of verification, such as a one-time code from a mobile app or SMS, in addition to their password.
- Regularly Update Security Practices: Stay up-to-date with the latest security practices and vulnerabilities. Regularly update your hashing algorithms and password storage mechanisms to adapt to evolving threats.
By implementing these comprehensive methods for storing user passwords, you can significantly enhance the security of your React application's authentication system. Protecting user passwords is not just a best practice; it's a fundamental step in building trust and ensuring the privacy of your users' data.
Token Management Strategies: Ensuring Consistent Security on the Server
Effective token management on the server side is essential for maintaining security and integrity within your React application's authentication system. Employing well-thought-out strategies helps prevent security breaches and ensures a consistent user experience.
- Token Storage and Encryption: Store authentication tokens securely on the server. Avoid storing tokens in client-side storage like cookies or local storage, as they are susceptible to theft through XSS attacks. Instead, use HTTP-only cookies to store tokens, which are more secure. Ensure that tokens are encrypted and signed to prevent tampering. JSON Web Tokens (JWTs) are a popular choice, providing both encryption and signature capabilities. Employ strong encryption algorithms and regularly update encryption keys.
- Token Expiration: Implement token expiration to limit the window of vulnerability. JWTs can include an expiration timestamp, ensuring that tokens become invalid after a certain period. Shorter token lifetimes, coupled with automatic renewal mechanisms, enhance security.
- Token Revocation: Develop a mechanism for token revocation in case of security breaches or user logouts. Maintain a blacklist of revoked tokens on the server. When a user logs out or their account is compromised, add their token to the blacklist to prevent further access.
- Rate Limiting and Throttling: Protect against brute-force attacks by implementing rate limiting and throttling for token-based requests. Limit the number of requests a client can make within a specified timeframe to deter malicious activities.
- Token Refresh Mechanism: Utilize token refresh mechanisms to maintain user sessions without requiring frequent login. When a token is close to expiration, the client can request a new token using a refresh token, reducing the disruption to the user experience.
- Auditing and Monitoring: Implement robust auditing and monitoring of token-related activities. Log token creation, usage, and expiration events. Set up real-time alerts for suspicious activities, such as an unusual number of token refresh requests.
- Secure Token Transmission: Always transmit tokens securely over HTTPS. Avoid including tokens in URL parameters or request bodies. They should only be transmitted in the Authorization header or HTTP-only cookies, which are more resistant to interception.
- Cross-Origin Resource Sharing (CORS): Configure CORS policies to control which origins can access your APIs. Restrict access to trusted domains to prevent cross-site request forgery (CSRF) attacks.
- Regular Security Audits: Conduct regular security audits and penetration testing to identify vulnerabilities in your token management system. Address any identified issues promptly to maintain a strong security posture.
- Regulatory Compliance: If your application deals with sensitive user data, ensure that your token management strategies align with data protection regulations like GDPR. Implement encryption, access controls, and data anonymization as necessary.
By implementing these token management strategies, you can maintain a consistent and robust security posture on the server side of your React application. This not only protects sensitive user data but also fosters trust among users, ensuring a secure and reliable user authentication experience.
Exploring Additional Security Layers: Two-Factor Authentication
Two-factor authentication (2FA) is an invaluable and sophisticated security enhancement within the realm of a React application's authentication system. It introduces an additional layer of safeguarding by demanding users to furnish not just one, but two distinct forms of identity verification before gaining access. This essay delves into the effective integration of 2FA, elucidating its significance and outlining the best practices to implement it seamlessly.
At the heart of 2FA lies the amalgamation of authentication methods, a fusion of something the user knows, typically a password, with something the user possesses, such as a mobile device. Two prominent methods in this realm include One-Time Password (OTP) and Biometric Verification. OTPs, often delivered via email, SMS, or a specialized authentication app like Google Authenticator, provide users with time-sensitive codes. Meanwhile, biometric verification harnesses the convenience and security of fingerprint or facial recognition on compatible devices.
The journey towards effective 2FA implementation commences with user enrollment. During the registration or account setup phase, users should be not just encouraged but also guided towards enabling 2FA. The process should be user-friendly, offering clear instructions and multiple options for 2FA methods.
To mitigate the risk of being locked out due to lost or inaccessible primary 2FA methods, the provision of backup codes is essential. These codes serve as a lifeline and should be issued securely, with mechanisms in place to regenerate them as necessary.
The underpinning of secure 2FA is the safeguarding of sensitive data, including secret keys for OTPs. Strong encryption should be employed to shield this information from prying eyes. Storage of these secrets in plain text or their exposure to the client side must be categorically avoided.
The verification process during login is a pivotal juncture for 2FA. Users should be prompted for their second authentication factor after providing their password. Verification of the 2FA code or biometric data should be conducted server-side to preempt any client-side manipulation.
For user convenience, the option to mark devices as "trusted" should be provided, facilitating a smoother login experience on frequently used devices. However, user autonomy should remain intact, allowing them to revoke trusted device status whenever they deem it necessary.
A cornerstone of security, rate limiting should be in place to thwart brute-force attacks. After a predefined number of failed 2FA attempts, the system should introduce delays or temporarily lock the account.
Educating users about the pivotal role of 2FA in enhancing their account security is paramount. Clear and comprehensive instructions on setting up and using 2FA should be readily available.
In the realm of security, vigilance is key. Logging all 2FA attempts and monitoring for any unusual or suspicious activities is indispensable. This proactive approach aids in the timely detection and response to potential security breaches.
Lastly, a contingency plan in the form of fallback mechanisms is crucial. In the event a user loses access to their 2FA method, a secure process for account recovery must be in place. This often involves alternative means of identity verification, such as email or customer support, ensuring that users can regain access to their accounts in a secure and structured manner.
By integrating 2FA into your React application's authentication system, you significantly enhance security, protecting user accounts from unauthorized access, even if passwords are compromised. It's a valuable feature that empowers users to take control of their account security and adds an extra layer of trust to your application.
Frontend Authentication Workflow
Safeguarding Routes: Design Principles for Protected Routes
In a React application with user authentication, safeguarding routes is essential to control access to specific sections or features based on user authentication status. Implementing protected routes ensures that only authorized users can access sensitive areas. Here are design principles for creating and managing protected routes:
- Route Configuration: Define a clear and structured route configuration that includes information about whether a route is public or protected. This configuration should be accessible to both the front end and back end to enforce access controls consistently.
- Authentication Context: Leverage the authentication context, which contains user authentication information, to determine whether a user is logged in. This context can be used to decide whether to grant access to protected routes.
- Route Guards: Implement route guards, functions that are executed before rendering a protected route. These guards can check the user's authentication status and redirect them to a login page if necessary.
- Private Route Component: Create a custom "PrivateRoute" component that encapsulates the logic for protecting routes. This component can take in a reference to the authentication context and the target route, making it reusable across the application.
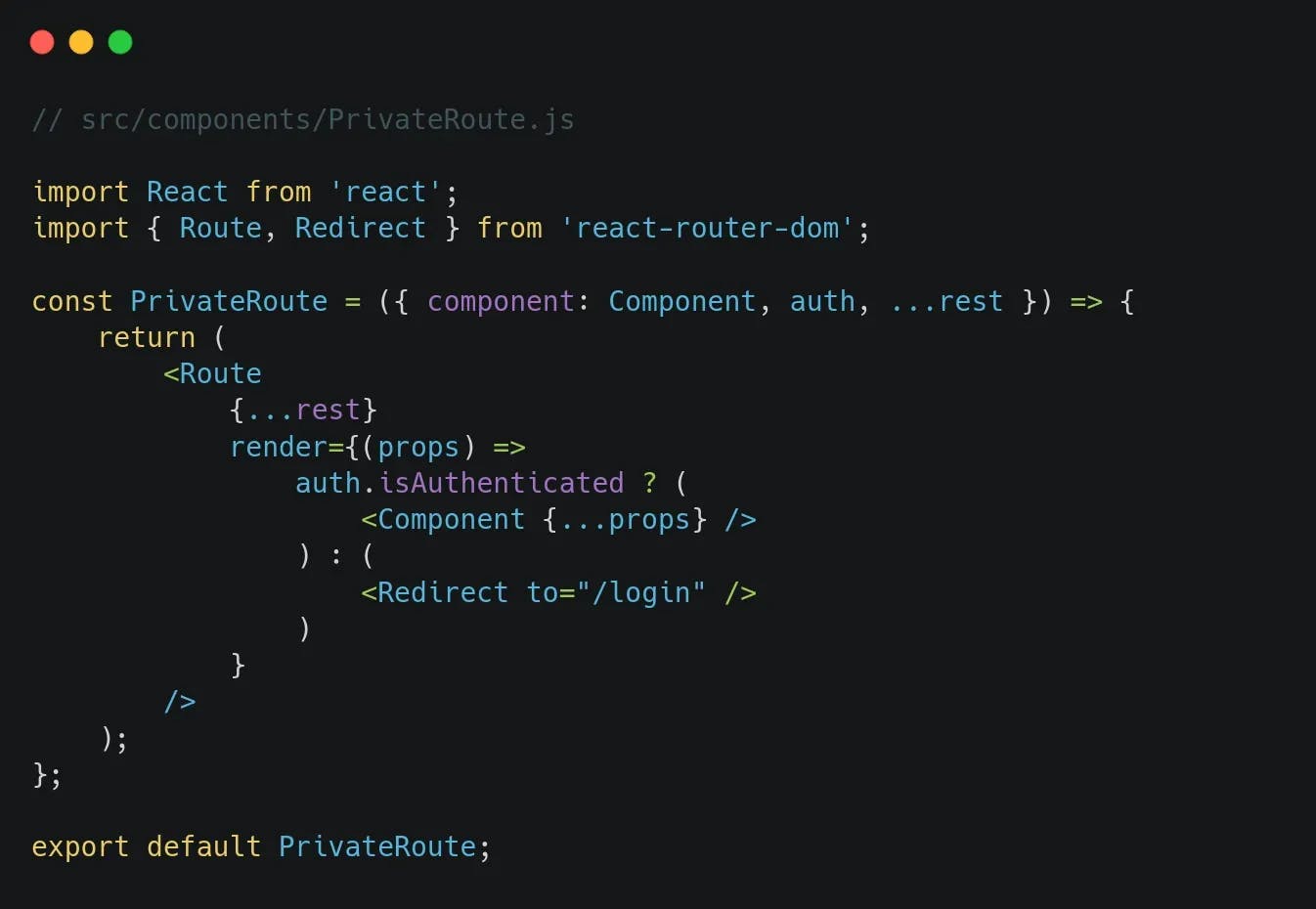
- Route Usage: Apply the "PrivateRoute" component to routes that require authentication. This ensures that only authenticated users can access these routes. For example:

- Redirects and Messages: Implement redirects to the login page when unauthorized access is attempted. Optionally, display informative messages to users explaining the reason for the redirection and prompting them to log in.
By following these design principles and utilizing route guards and custom components, you can effectively safeguard routes in your React application, ensuring that sensitive sections are only accessible to authenticated users. This not only enhances security but also provides a smoother and more controlled user experience.
Building User Sessions: A Deep Dive into Token-Based Mechanisms
Establishing and managing user sessions constitutes a fundamental aspect of user authentication in a React application. Central to this process is token-based mechanisms, which are pivotal in ensuring a smooth and secure user experience.
- Token-Based Authentication: Token-based authentication relies on the exchange of tokens between the client, typically a web browser, and the server. Tokens, exemplified by JSON Web Tokens (JWTs), function as digital keys that authenticate users without the necessity of storing session data on the server. This approach aligns seamlessly with stateless and scalable architectures.
- Token Generation: Upon a user's login, the server generates a token containing information about the user's identity and potentially additional claims, including an expiration time. Subsequently, this token is securely transmitted to the client, typically through an HTTP-only cookie or within the response body.
- Token Verification: In subsequent requests, the client incorporates the token within the request header or cookie. The server authenticates the token's validity by verifying its signature and expiration, thereby confirming the client's possession of valid authentication credentials.
- Statelessness: Token-based authentication fosters server statelessness, obviating the need to store session data. This simplifies server maintenance, encourages scalability, and facilitates deployment in distributed environments.
- Token Expiration and Renewal: Tokens are assigned a finite lifespan to bolster security. As a token approaches expiration, the client has the option to request a new token using a refresh token or by re-authenticating. This minimizes disruptions to the user experience while preserving security.
- Single Sign-On (SSO): Token-based mechanisms can also facilitate Single Sign-On (SSO) solutions, enabling users to access multiple applications with a solitary authentication event. This streamlines the user experience and diminishes the need for repetitive logins.
- Revocation and Logout: For maintaining control over user sessions, it is imperative to institute mechanisms for token revocation and user logout. Revoking a token renders it ineffectual for future requests, ensuring that users can securely log out.
- Cross-Origin Resource Sharing (CORS): Implement robust CORS policies to govern which origins can access your token-based APIs. This preventive measure thwarts unauthorized access and cross-site request forgery (CSRF) attacks.
- Monitoring and Auditing: Establish comprehensive monitoring and auditing protocols for activities related to tokens. This encompasses recording token issuance, utilization, and revocation events, as well as configuring real-time alerts for any suspicious activities.
Token-based mechanisms form the foundation of user sessions in modern React applications. By understanding and implementing these mechanisms effectively, developers can build secure, stateless, and scalable authentication systems that provide a seamless and protected user experience.
Providing a Graceful Exit: The Logout Functionality Unveiled
Logout functionality plays a pivotal role in the authentication system of a React application, offering users a secure means to end their sessions while upholding both security and trust. When executed effectively, logging out ensures a graceful departure from the application, emphasizing the importance of maintaining user confidence.
At its core, the process of logging out revolves around clearing the user's authentication state. This initial step entails the removal or invalidation of the authentication token or session on both the client and server sides, a standard practice in token-based authentication. On the client side, the token is deleted or marked as invalid, while the server takes action to invalidate the user's session or token upon receiving a logout request.
To safeguard against token reuse post-logout, the implementation of a token blacklisting mechanism is advisable. This mechanism places the user's token on a blacklist, effectively rendering it unusable for any subsequent requests, reinforcing the security of the application.
After ensuring the integrity of the authentication state, the user is redirected to a neutral page, typically the login page or home page. This redirection serves as a clear indicator that the user is no longer authenticated, facilitating a seamless transition.
Providing user feedback is a crucial aspect of the logout process. Communicating the successful completion of the logout operation through messages or notifications enhances the user experience, ensuring transparency and user-friendliness.
Another fact to consider is the protection of routes. Following logout, it is imperative to restrict access to protected routes, rerouting any attempts to access such resources to the login page or an appropriate error page.
For applications employing server-side sessions, session termination on the server side is vital. This action releases any associated resources or locks, a particularly significant consideration for applications involving concurrent access or sensitive operations.
Clearing local storage or session storage, if used for temporary data storage, is a prudent measure during logout to remove sensitive information, including tokens or session data, mitigating any potential security risks.
In the interest of auditing and security monitoring, logging logout events is advisable. This practice helps in tracking user actions and establishing an audit trail in the event of security incidents.
For systems involving token revocation, such as OAuth 2.0, it is imperative to ensure the revocation of the user's tokens, rendering them unusable for further authentication attempts.
The implementation of a well-designed logout functionality not only bolsters security but also elevates the user experience within your React application. It fosters trust and confidence among users, underlining the significance of this often-overlooked aspect of authentication system design.
Best Practices for User Authentication in React
The Ever-Evolving Landscape: Importance of Keeping Dependencies Updated
Maintaining up-to-date dependencies is a critical aspect of developing a secure and robust React application with user authentication. The software landscape is ever-evolving, and staying current with dependencies helps ensure that your authentication system remains secure, performant, and compatible with the latest standards.
- Security Vulnerabilities: One of the primary reasons for keeping dependencies updated is to address security vulnerabilities. As new vulnerabilities are discovered, package maintainers release patches and updates to fix these issues. Failing to update dependencies can leave your application exposed to known security threats.
- Compatibility and Performance: Updates often include improvements in compatibility with the latest versions of libraries, frameworks, and browsers. They may also optimize code for better performance. By staying updated, you can ensure that your application remains compatible and runs efficiently on various platforms.
- Bug Fixes: Dependency updates often include bug fixes that resolve issues and improve the overall stability of your application. Ignoring these updates can lead to unexpected errors and downtime.
- New Features and Enhancements: Updates can introduce new features and enhancements that can benefit your application. These additions may include improved user authentication methods, more efficient algorithms, or better user experiences. Embracing these updates can keep your application competitive and user-friendly.
- Deprecation and End-of-Life: Dependencies have life cycles, and older versions may become deprecated or reach end-of-life. When this happens, they may no longer receive updates or support, leaving your application at risk. Keeping dependencies updated ensures that you are using actively maintained and supported packages.
- Dependency Chains: Dependencies often have their dependencies, forming a chain of interconnected packages. Updating a single package can sometimes resolve issues or vulnerabilities in multiple parts of your application.
- Manual Review: When updating dependencies, it's an opportunity to review and assess any changes or new features introduced by the updated packages. This ensures that the updates align with your project's requirements and goals.
- Automated Tools: Utilize automated dependency management tools like npm audit or yarn audit to identify and address known vulnerabilities in your project. These tools can streamline the process of keeping dependencies secure.
- Testing and Regression: After updating dependencies, conduct thorough testing to ensure that your application still functions as expected. Regression testing helps identify any unintended side effects of updates.
By embracing the importance of keeping dependencies updated, you can proactively address security vulnerabilities, improve compatibility and performance, and ensure that your React application's user authentication system remains robust and reliable in the ever-evolving software landscape.
Conclusion
In the vast and intricate landscape of modern software development, where complexity intertwines with innovation, the journey of crafting a React application with a resilient user authentication system has unfolded. Throughout this essay, we have delved into the intricate details, the intricate web of choices, and the methodologies that underpin the creation of an authentication system that stands as a fortress against the relentless tides of security threats, and yet, serves as a gateway to seamless user experiences.
From the imperative role of user authentication to the exploration of token-based mechanisms, the blueprint for RESTful APIs, the grace of graceful logout, and the adoption of additional security layers like Two-Factor Authentication, we have traversed diverse terrains. Each topic is a piece of the puzzle, meticulously designed to fit within the broader context of an authentication system that delivers both security and user-friendliness.
In the ever-evolving landscape of technology, we emphasized the paramount importance of keeping dependencies updated. As we navigated this terrain, we recognized that neglecting this facet could expose an application to the lurking shadows of vulnerabilities, whereas embracing it could lead to a fortified and dynamic software ecosystem.
Yet, beyond the technical intricacies and methodologies, a deeper philosophy emerges. It's the pursuit of order amidst the chaos, the commitment to truth and transparency, and the resilience to evolve with the shifting sands of technology and security. It's the recognition that every line of code, every design choice, and every security measure should serve the ultimate goal – empowering users to access digital realms securely and seamlessly.
As we conclude this comprehensive essay, we leave behind a trail of insights, guidelines, and best practices. However, we must acknowledge that the journey is far from over. The world of software development remains an uncharted territory, where innovation and challenges will continue to emerge.
So, dear React developer as you embark on your journey of building and securing React applications, may you find wisdom in these pages. May you persist in your quest to bring order to the digital chaos and empower users with the highest standards of security and usability. May you always remain open to the ever-evolving landscape, ready to adapt and innovate in the pursuit of excellence.
Author

Dhawal Pandya
Dhawal Pandya is a Software Developer with an optimal Venn Diagram of skills including JavaScript, ReactJS, Python, and Writing. He is always found learning new technologies and contributing to the community.
Frequently Asked Questions

Press

Blog
