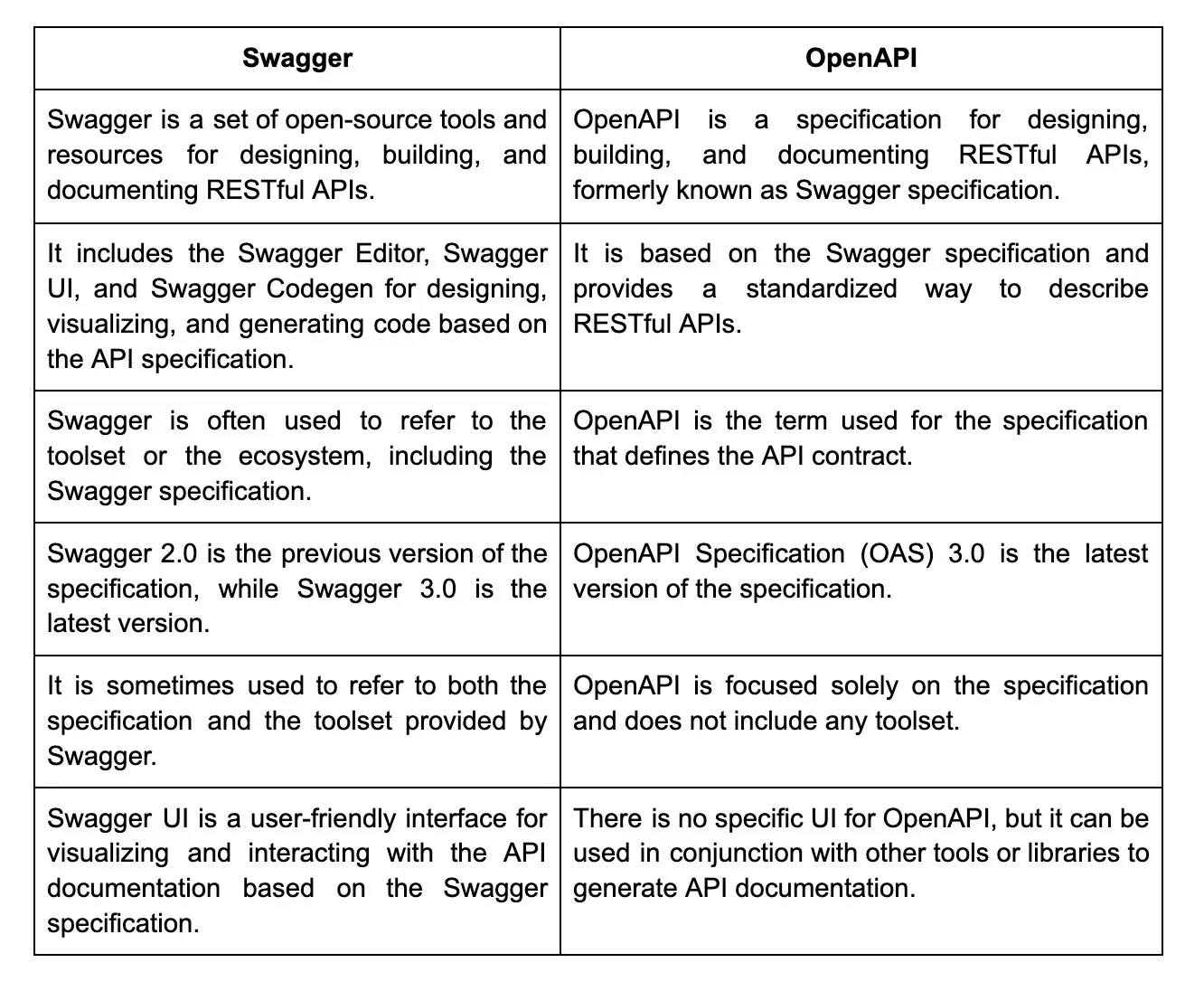
REST/RESTful APIs
Basic Interview Q&A
1. Can you explain the concept of resources in RESTful web services?
In RESTful web services, resources are the key concept. A resource represents an entity or an object such as a user, a product, or an order. It can be anything that can have its own unique identifier and can be accessed and manipulated through the web service.
Each resource is represented by a unique URL or URI (Uniform Resource Identifier). For example, in an e-commerce system, a product resource could be represented by the URL /products/{productId}, where {productId} is the identifier of a specific product.
Resources can be operated upon using different HTTP methods such as GET, POST, PUT, and DELETE. These methods are mapped to common CRUD (Create, Read, Update, Delete) operations. For example, a GET request to retrieve the details of a product resource, a POST request to create a new product resource, or a DELETE request to remove a product resource.
2. What are the HTTP Methods?
GET: This method is used to retrieve data from the server.
Example: GET http://www.example.com/api/users
POST: This method is used to create new data on the server.
Example: POST http://www.example.com/api/users
PUT: This method is used to update existing data on the server.
Example: PUT http://www.example.com/api/users/1
DELETE: This method is used to delete existing data on the server.
Example: DELETE http://www.example.com/api/users/1
PATCH: This method is used to partially update existing data on the server.
Example: PATCH http://www.example.com/api/users/1
HEAD: This method is similar to GET, but it only retrieves the headers of the response, and not the body.
OPTIONS: This method is used to retrieve information about the communication options available for a resource.
3. What is HATEOAS and how is it used in RESTful web services?
HATEOAS stands for "Hypermedia as the Engine of Application State"1. It is a constraint in the REST architectural style that allows a client to navigate a web service dynamically through hypermedia links embedded in the responses. In other words, HATEOAS enables the server to provide not only the requested data but also the available actions or resources that the client can interact with.
In a RESTful web service, HATEOAS is used to provide discoverability and self-descriptive interactions. It allows clients to understand the available resources and actions by following the hypermedia links provided in the responses. This means that instead of having prior knowledge or hardcoding the URLs for different operations, the client can dynamically discover and navigate the available resources and actions based on the provided links.
By using HATEOAS in RESTful web services, the client becomes more decoupled from the server and is able to evolve independently. The client only needs to know the entry point or initial URL of the web service, and from there, it can navigate the available resources and actions based on the hypermedia links provided in the responses. This makes the web service more flexible, extensible, and adaptable to changes over time.
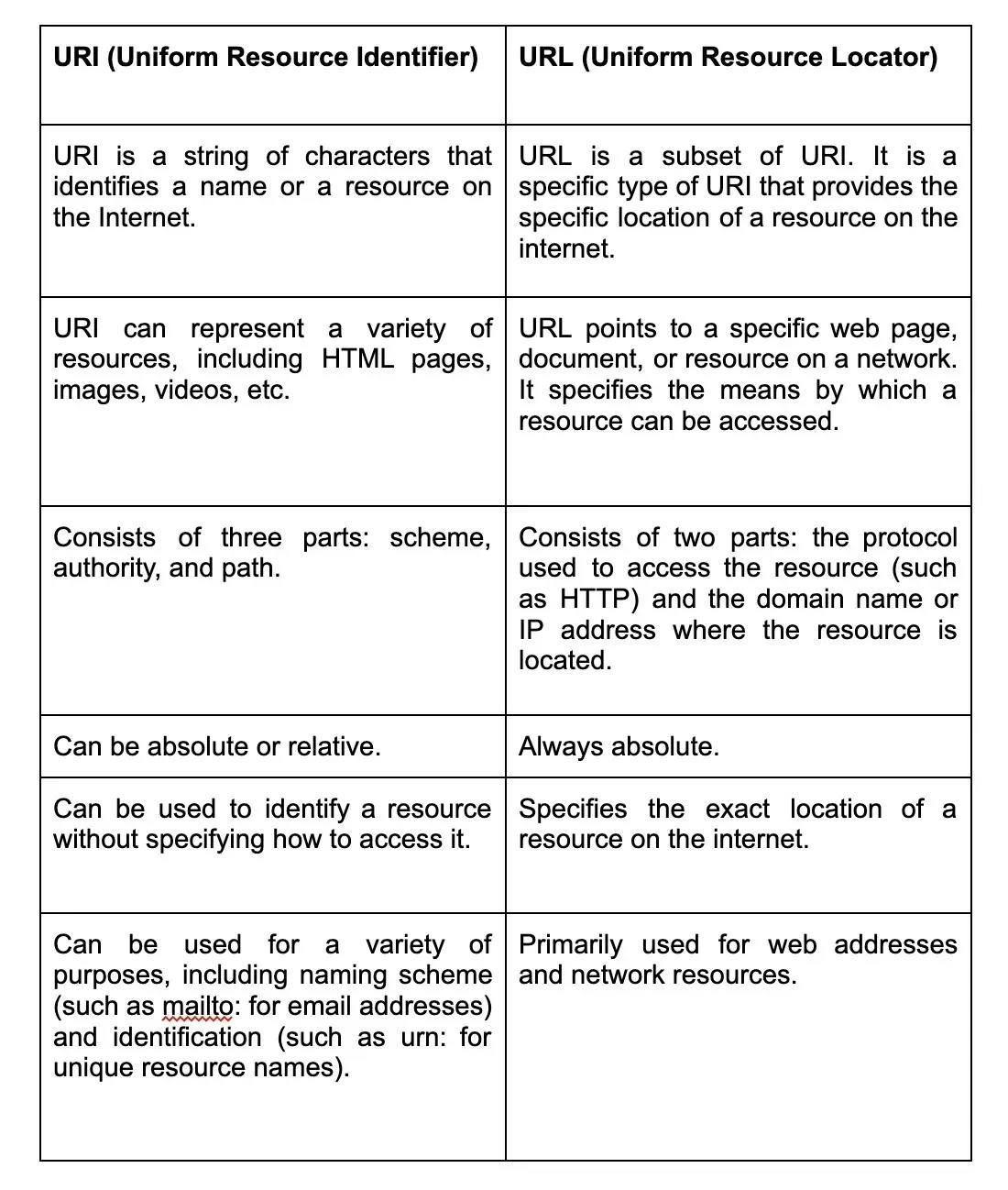
4. What is the difference between URI and URL?
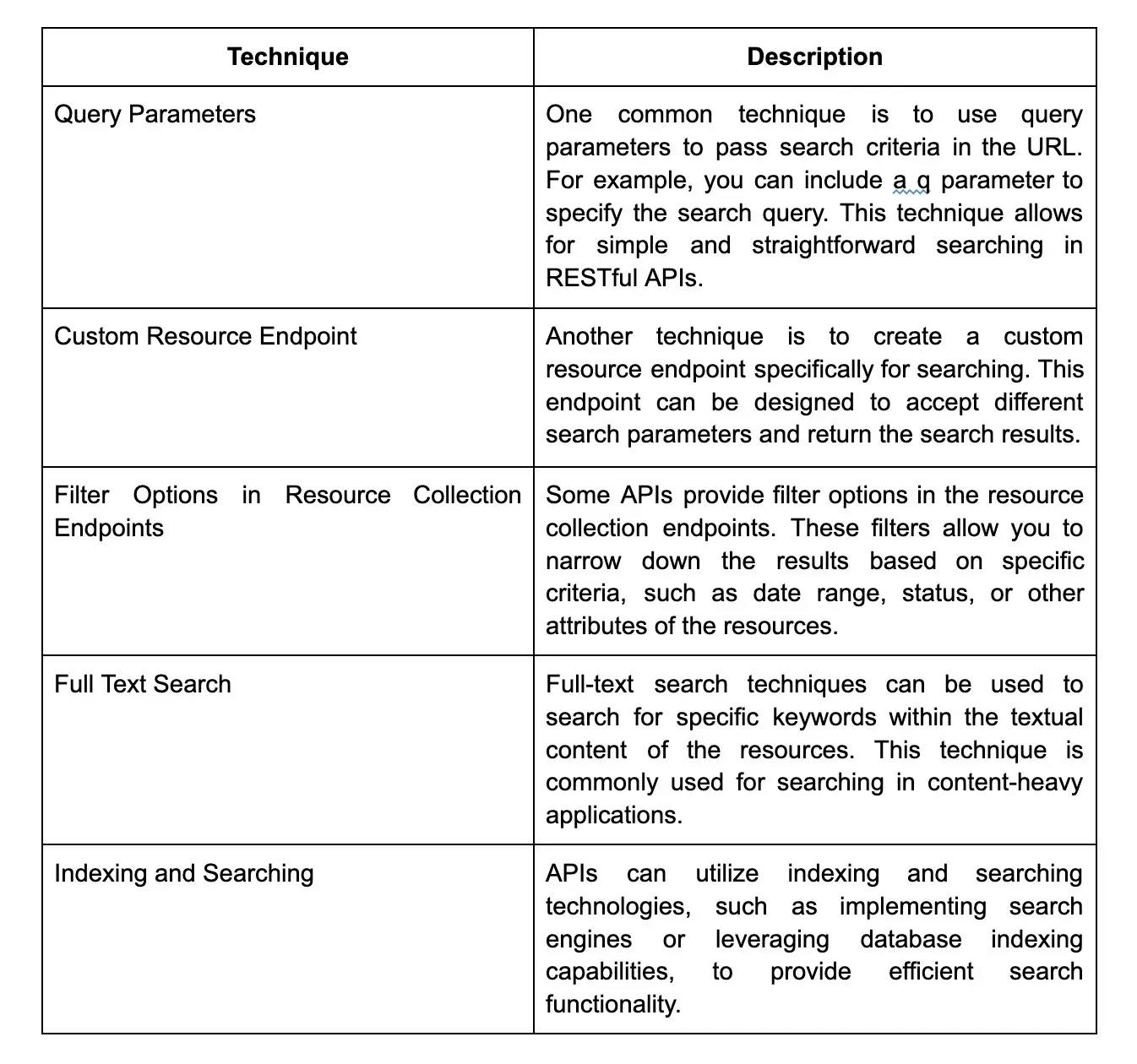
5. How do you handle errors in RESTful web services?
- Returning appropriate HTTP status codes: Each error response should have an appropriate HTTP status code that indicates the nature of the error. Common status codes for errors include 400 Bad Request, 401 Unauthorized, 403 Forbidden, and 404 Not Found.
- Providing meaningful error messages: Along with the HTTP status code, you should include a detailed error message in the response body. This message should help the client understand what went wrong and how to resolve the issue.
- Consistent error response format: It's a good practice to follow a consistent error response format across all the API endpoints. This makes it easier for clients to handle and parse error responses.
- Handling exceptions and returning custom errors: In your code, you should catch any exceptions or errors that occur during request processing and convert them into appropriate error responses. This ensures that clients receive consistent error responses regardless of the type of error.
- Logging: Logging the details of the error can be helpful for debugging purposes. It allows you to track issues, analyze trends, and make improvements to the web service.
6. Can you explain the concept of versioning in RESTful web services?
- In RESTful web services, versioning refers to the practice of identifying and managing different versions of the API that a client can use. Versioning allows developers to introduce changes to an API, while still providing backwards compatibility to older clients that need to continue functioning with the previous version.
- There are several ways that versioning can be implemented in RESTful web services. One common approach is to include the version number in the URL of each API endpoint.
- Versioning helps ensure that changes to an API do not break existing client applications that rely on it, while at the same time allowing new features and improvements to be introduced.
7. Can you tell what constitutes the core components of HTTP requests?
- Request Line: This contains the HTTP method, such as GET, POST, PUT, DELETE, which specifies the desired action to be performed on the resource.
- Headers: Headers provide additional information about the request, such as the content type, Accept-Encoding, cookies, authentication credentials, and more.
- Body: The request body is an optional component and is used to send data to the server, typically in the case of POST or PUT requests.
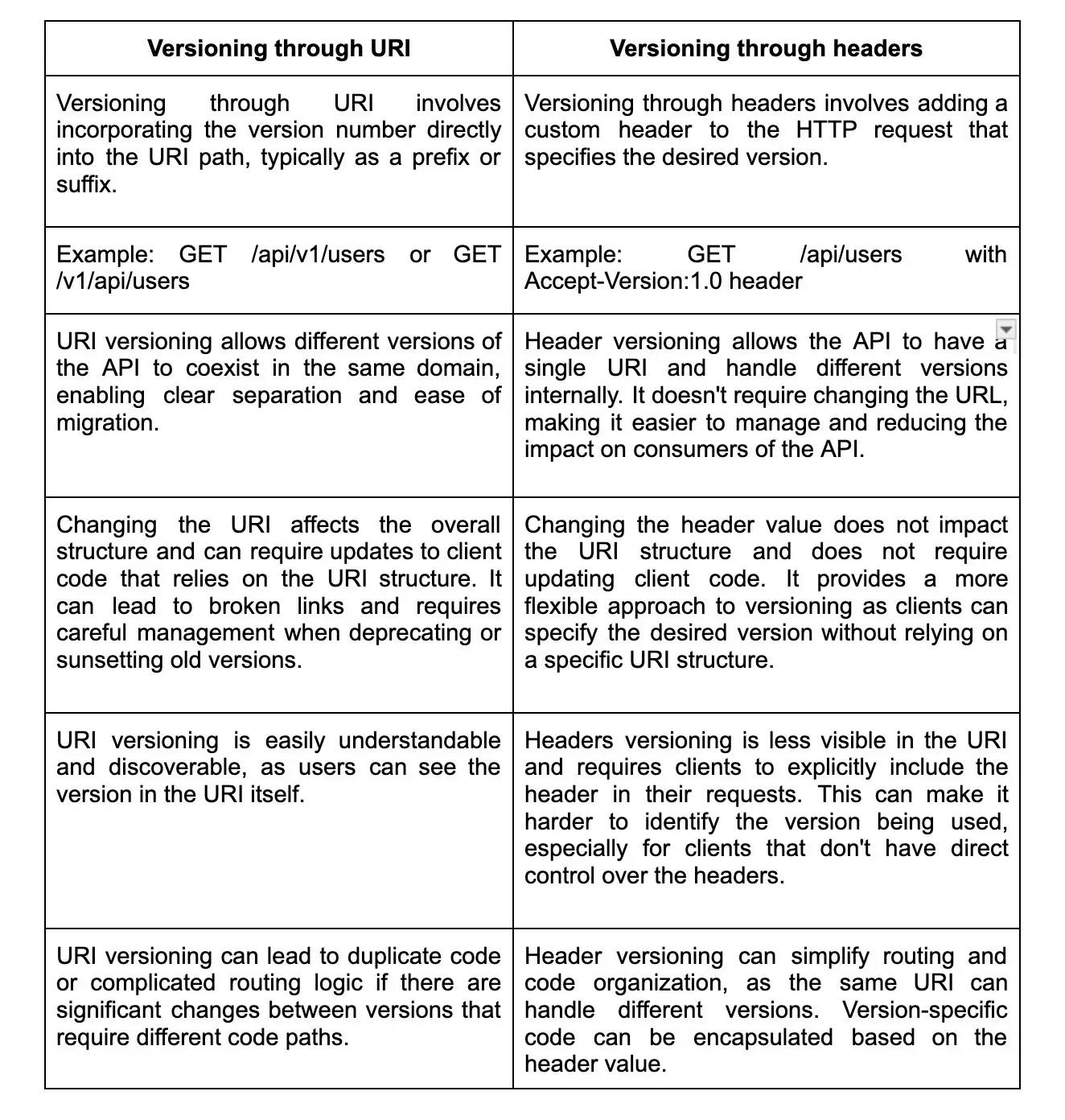
8. What is the difference between versioning through URI and through headers?
9. What is content negotiation in RESTful web services?
- Content negotiation in RESTful web services is the process of determining the most suitable representation of a resource that can be returned to the client based on the client's preferences[1]. When a RESTful web service receives a request, the client can specify certain preferences such as the preferred media type, language, or content encoding. The server uses content negotiation to select the appropriate representation of the resource that matches the client's preferences.
- Content negotiation allows for flexibility in serving different representations of the same resource to clients with varying requirements. For example, a client may prefer to receive JSON data, while another client may prefer XML. By using content negotiation, the server can choose the best representation for each client, promoting interoperability and improving the user experience.
- In RESTful web services, content negotiation is typically performed using the Accept header in the HTTP request[2]. The client includes the Accept header, specifying the desired media types or content types it can handle. The server then examines the Accept header and selects the appropriate representation based on the available options and the client's preferences.
10. What constitutes the core components of HTTP Response?
- Status Line: The status line contains the HTTP version, the status code, and the reason phrase. It provides information about the status of the response, indicating whether the request was successfully processed or if there was an error.
- Headers: Headers provide additional information about the response, such as the content type, content length, caching directives, and more. They are key-value pairs that provide metadata about the response.
- Body: The response body contains the actual data or resource requested by the client. It can be in various formats such as HTML, JSON, XML, or plain text.
11. What are the different media types used in content negotiation?
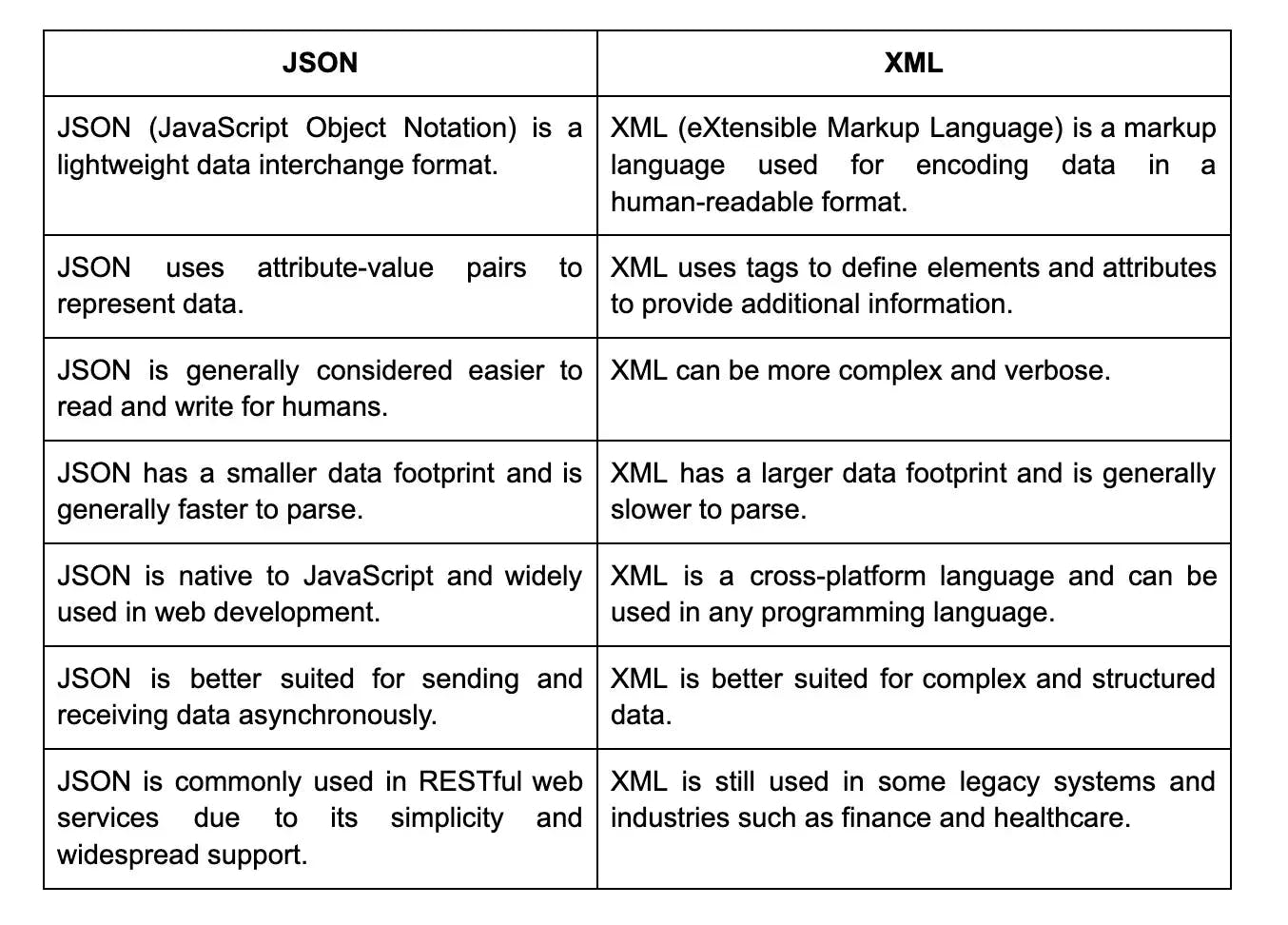
- JSON (JavaScript Object Notation): JSON is a lightweight data interchange format that is widely used in web applications for transmitting data between a server and a client.
- XML (eXtensible Markup Language): XML is a markup language that is designed to store and transport data. It is commonly used for data exchange in web services and APIs.
- HTML (Hypertext Markup Language): HTML is the standard markup language for creating web pages. It is commonly used in content negotiation to deliver web content to clients.
- Plain text: Plain text refers to unformatted text that does not contain any markup or styling. It is often used for simple data representation in content negotiation.
- Images: Various image formats such as JPEG, PNG, and GIF can be used in content negotiation to transfer image data between a server and a client.
12. What is the concept of statelessness in REST?
The concept of statelessness in REST refers to the server not storing any information about the client's state between requests. In a stateless architecture, each request from the client to the server must contain all the necessary information for the server to understand and process the request. The server does not keep track of any session or state information about the client.
This means that each request is independent and self-contained, and the server does not need to store any client-specific information. The lack of state allows for better scalability and performance as the server does not need to manage or synchronize client state.
Statelessness also aligns with the principles of the REST architectural style, which emphasizes simplicity, scalability, and the uniform interface between clients and servers. It enables the server to be stateless, meaning it can be easily distributed across multiple servers or scaled horizontally without any impact on the overall system.
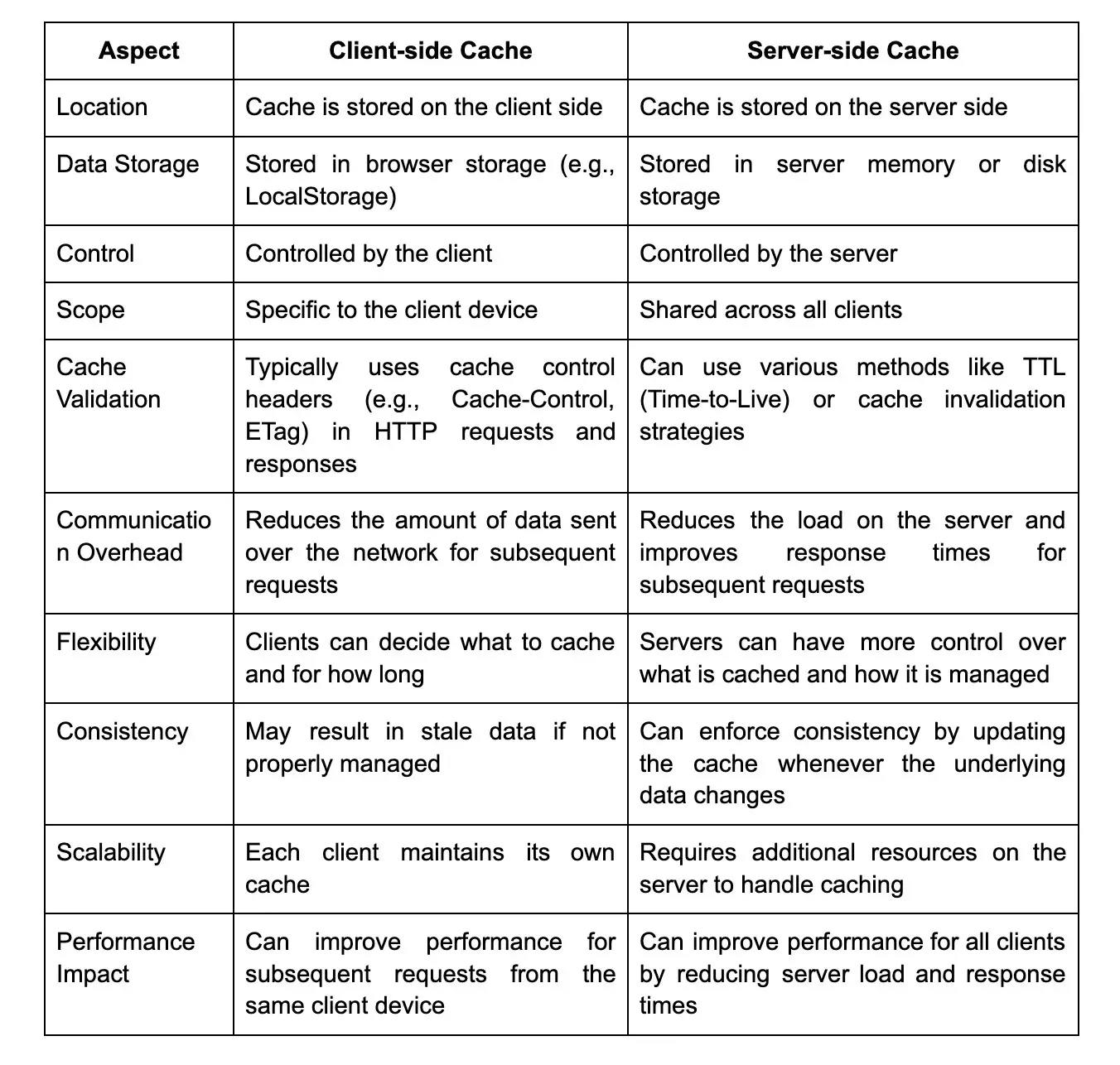
13. How do you implement caching in RESTful web services?
Caching in RESTful web services can be implemented using various strategies. One approach is to utilize the HTTP caching mechanisms, such as the Cache-Control header, which allows specifying caching directives like caching time duration, validation, and revalidation rules. This helps in storing response data in the client's cache and reducing the number of requests to the server. Additionally, server-side caching can be used, where response data is stored in memory or a persistent cache like Redis. The server can then check if the requested data is already cached and return it directly instead of processing the request again.
14. Can you explain the concept of conditional requests in RESTful web services?
In RESTful web services, conditional requests are a way for clients to only request data from a server if certain conditions are met. This can help improve performance and reduce unnecessary network traffic.
Two common types of conditional requests are "If-Modified-Since" and "If-None-Match". With "If-Modified-Since", the client sends a request with a timestamp indicating the last time it received the resource. If the resource has not been modified since that time, the server will respond with a 304 Not Modified status code, indicating the client can use its cached copy. With "If-None-Match", the client sends a request with an ETag, which is a unique identifier for the resource. If the ETag matches the current version of the resource on the server, the server will respond with a 304 Not Modified status code." Overall, using conditional requests can help save bandwidth and improve the responsiveness of RESTful web services.
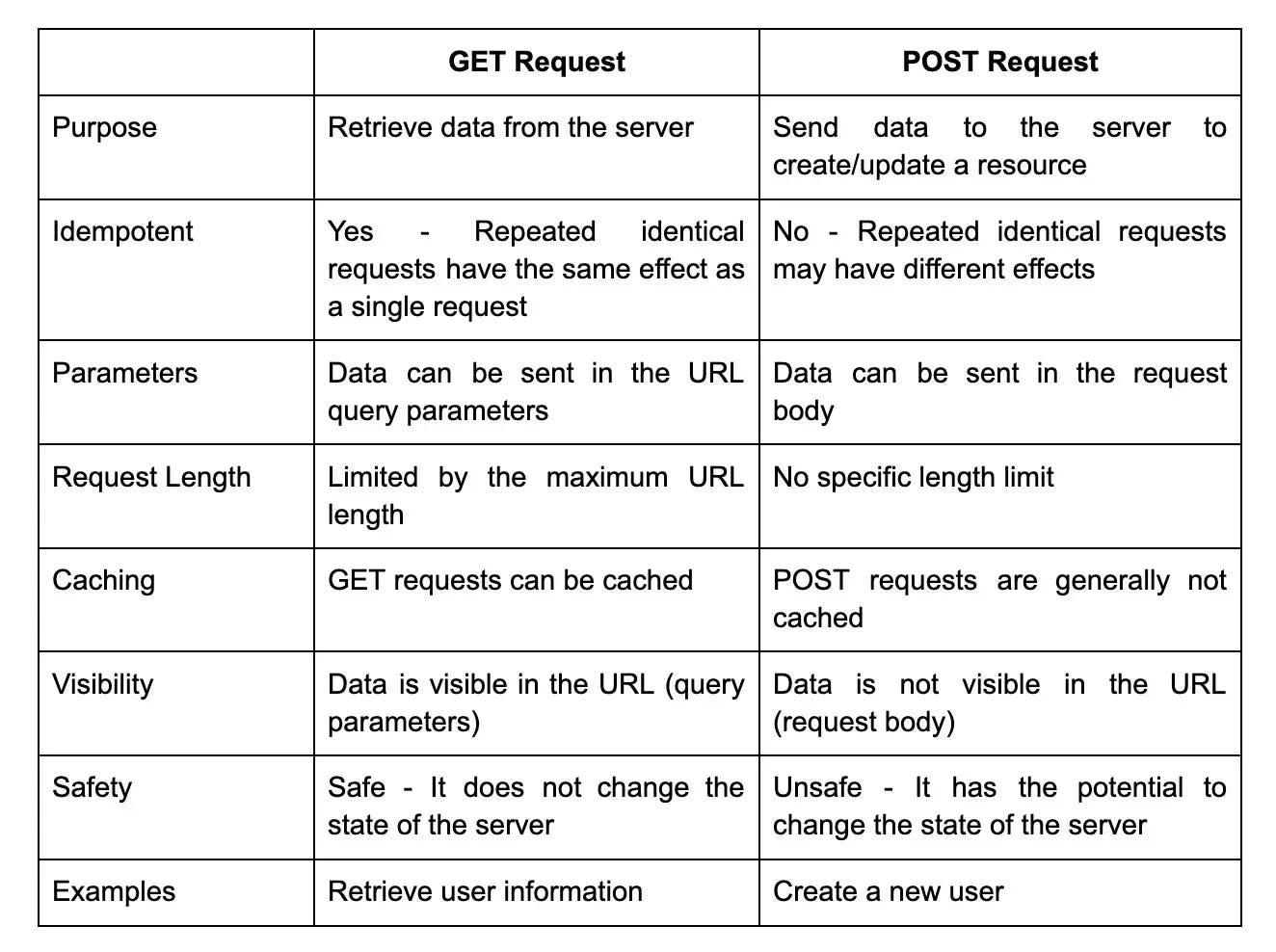
15. What is the difference between a GET request and a POST request in REST API?
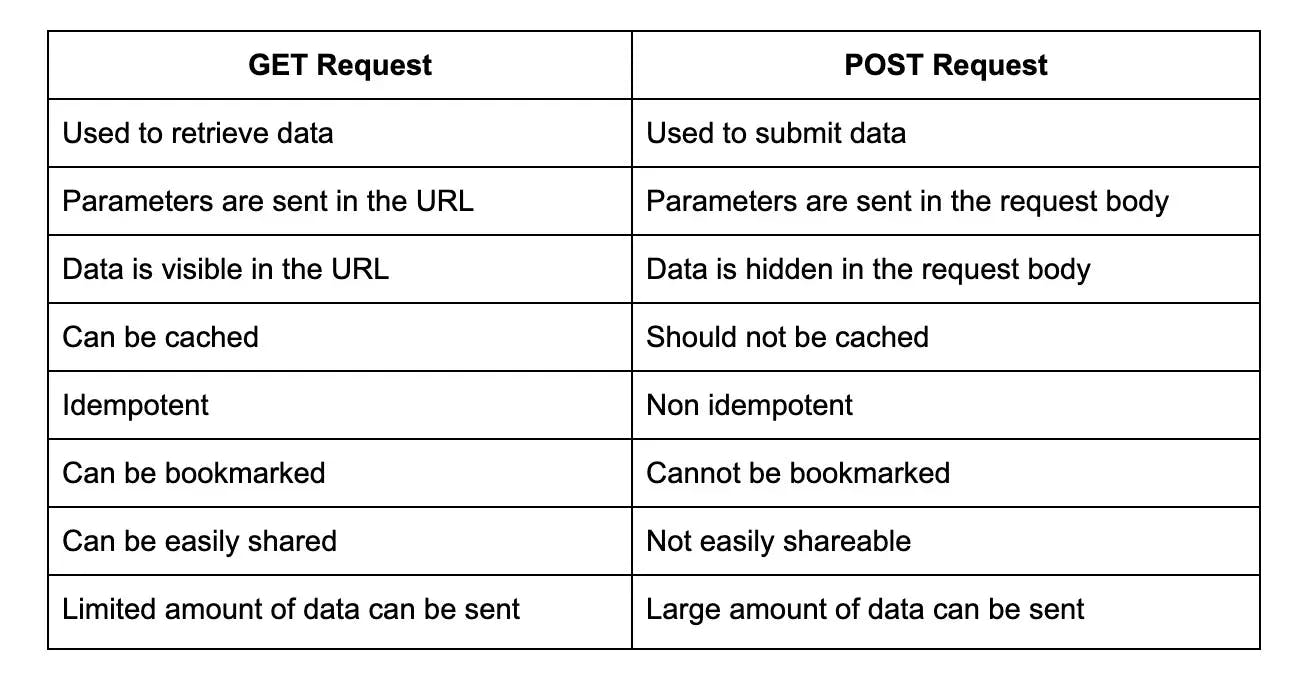
16. How do you secure a RESTful API?
To secure a RESTful API, there are several best practices that one can follow. First, ensure that all API requests are authenticated and authorized through a secure channel such as Transport Layer Security (TLS). Authentication credentials for each request should be validated on the server using techniques like OAuth2 and JWT tokens.
Additionally, APIs should be protected from common attacks such as Denial-of-Service (DoS) attacks by implementing rate limiting, threat analysis, and using web application firewalls . Finally, it is important to keep up with security trends and address any potential security breaches quickly.
17. What are the different types of authentication mechanisms used in RESTful web services?
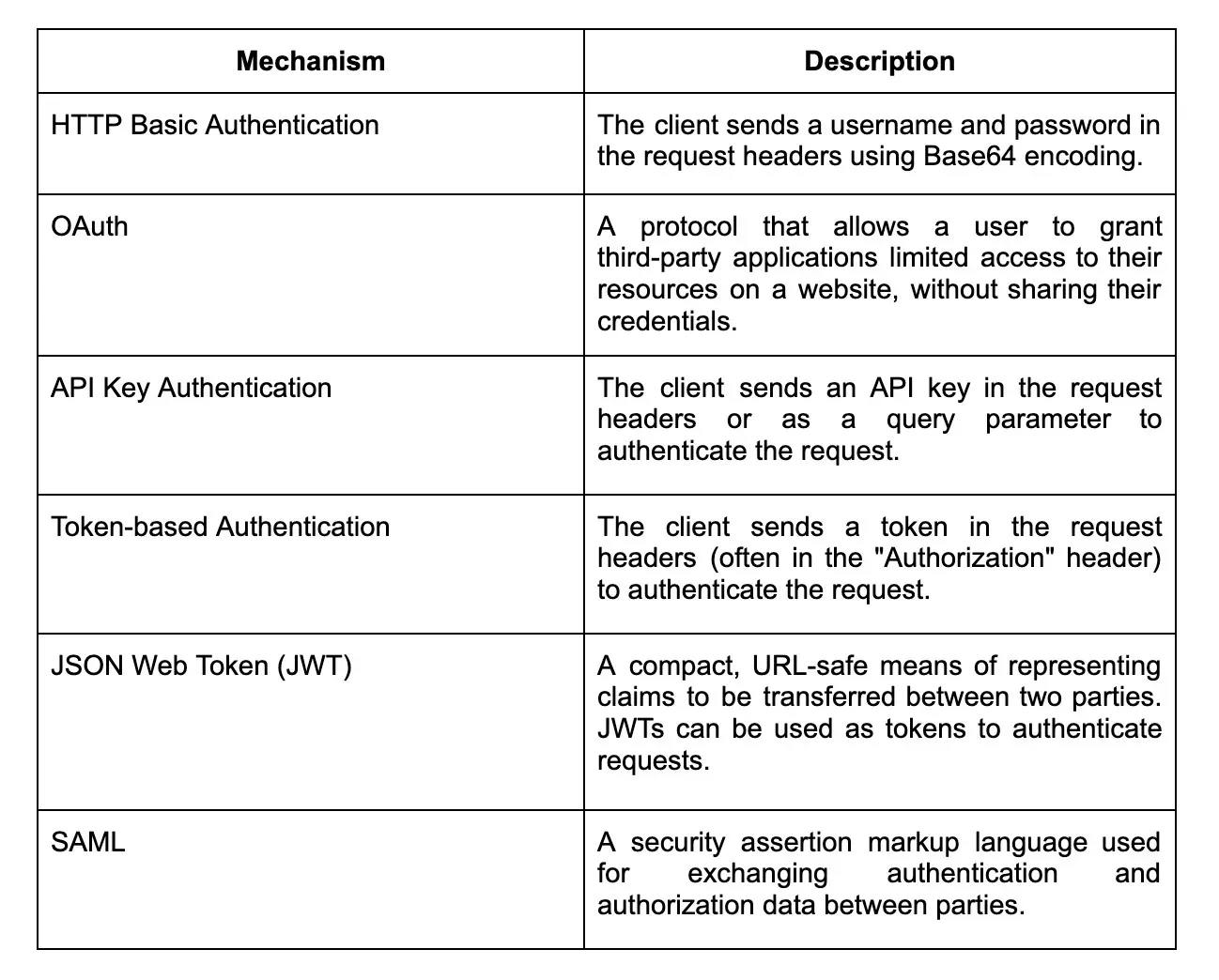
18. Can you explain the concept of token-based authentication?
Token-based authentication is a common method used to verify the identity of users accessing a system or application. It involves the use of a token, which is a unique and secure piece of information assigned to a user after successful authentication. This token serves as the user's proof of identity and is stored either on the server or the client-side.
When a user attempts to access a protected resource, they include this token in their request. The server then verifies the token's validity and, if valid, grants access to the requested resource. Token-based authentication eliminates the need for sending sensitive credentials in each request, improving security and scalability. Additionally, since tokens can be easily revoked and managed, it enhances the overall control and flexibility over user access.
19. How do you handle CORS in RESTful web services?
Cross-Origin Resource Sharing (CORS) is a mechanism that allows web browsers to make requests to a different origin than the current page. To handle CORS in RESTful web services, you can set the appropriate headers in the server response. This includes the "Access-Control-Allow-Origin" header, which specifies the allowed origins to access the resource. Additionally, you may need to handle preflight requests by including the "OPTIONS" method in your RESTful service and sending the appropriate response headers. This can be done by configuring the server or by using libraries or frameworks that handle CORS automatically, such as Spring Boot or Express.js.
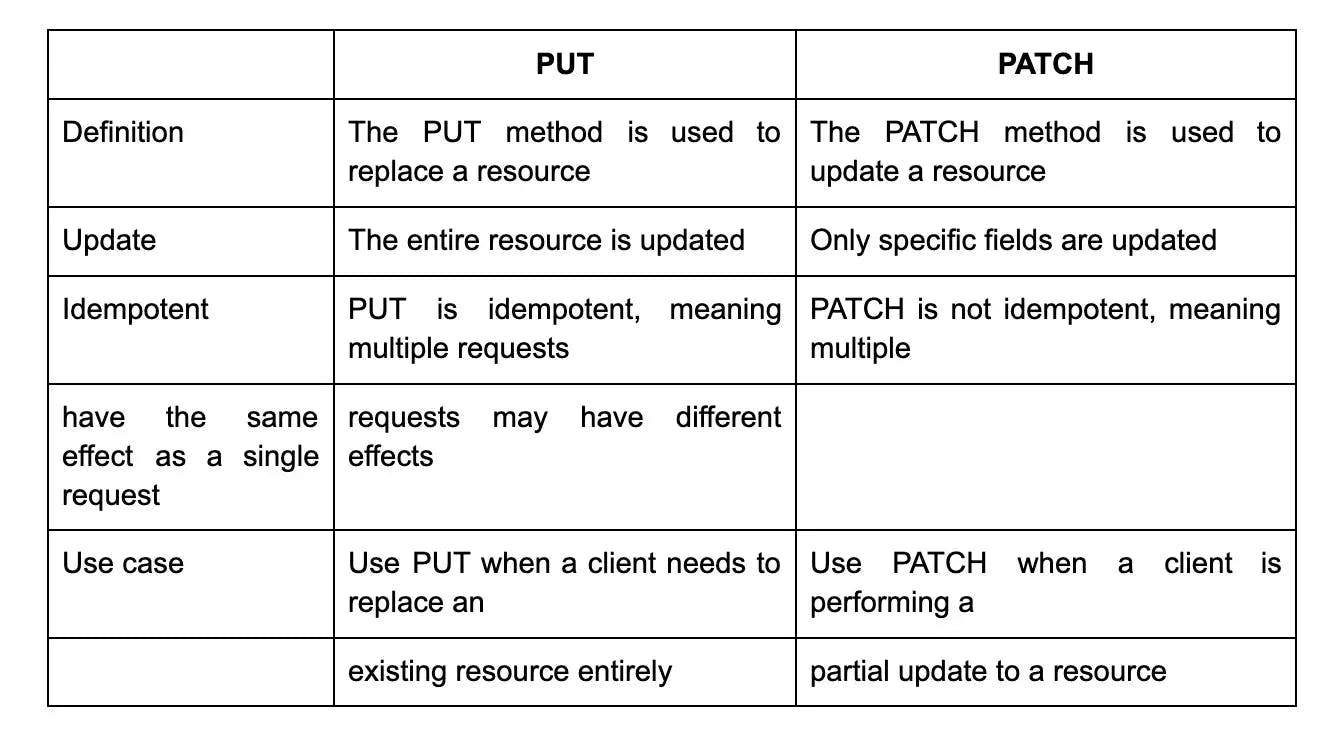
20. How does a PUT request differ from a PATCH request in REST API?
In REST API, both PUT and PATCH are used to update a resource. However, there are differences in how they operate.
A PUT request is used to completely replace the resource with a new version. It requires sending the entire updated resource as the request payload. PUT requests are idempotent, meaning that multiple identical requests will have the same effect as a single request.
On the other hand, a PATCH request is used to partially update a resource. It only requires sending the specific changes that need to be made in the request payload. PATCH requests are not necessarily idempotent, which means that multiple identical requests might have different effects depending on the server implementation. Overall, PUT is used for replacing a resource entirely, while PATCH is used for making partial updates to a resource.
21. Can you explain the concept of rate limiting in RESTful web services?
Rate limiting in RESTful web services is a technique used to control the number of requests a client can make within a given time period. It is implemented to prevent abuse, improve performance, and ensure fair usage of server resources.
By setting limits, such as the maximum number of requests per minute, an API can prevent clients from overwhelming the server and causing instability. Rate limiting can be implemented using various techniques like IP-based limiting, token-based limiting, or user-based limiting. It helps maintain the stability, availability, and security of the web service, ensuring a positive experience for all users.
22. How do you implement rate limiting in RESTful web services?
Rate limiting in RESTful web services can be implemented using various techniques. One common approach is to use token bucket algorithm. In this approach, each user or client is assigned a certain number of tokens that represent the maximum number of requests they can make within a specific time frame. With each request, the client consumes a token from their allocated bucket. If the bucket becomes empty, the client needs to wait or receive an error response.
Another approach is to use a sliding window algorithm, where the server maintains a window of fixed duration and counts the number of requests made within that window. If the number of requests exceeds a pre-defined limit, further requests are either delayed or rejected. Both these methods help in protecting the web service from abuse and ensure fair usage among clients.
23. What is API throttling and how is it used in RESTful web services?
API throttling is a technique used to limit the number of requests that can be made to a web service API within a specified time period. This helps to prevent overloading of the API server, which can cause service disruptions, slow response times, or even crashes.
In RESTful web services, API throttling can be implemented by setting limits on the number of requests that can be made per minute, hour, or day. The API gateway acts as a mediator between the client and the server, enforcing these limits and controlling the flow of requests to maintain optimal performance and stability. By using API throttling, RESTful web services can provide reliable and scalable access to their resources.
24. Can you explain the concept of load balancing in RESTful web services?
Load balancing is a technique used in RESTful web services to distribute incoming network traffic across multiple servers. The purpose is to optimize resource utilization, improve scalability, and enhance the overall performance of the system.
In load balancing, a load balancer acts as a mediator between the client and the servers. It receives the incoming requests and distributes them among the available servers based on various algorithms, such as round-robin or least connections. This ensures that no single server gets overwhelmed with excessive traffic, leading to increased reliability and responsiveness of the RESTful web service.
25. How do you implement load balancing in RESTful web services?
Load balancing in RESTful web services can be implemented using various techniques. One common approach is to use a load balancer that distributes incoming requests across multiple server instances. This can be achieved through technologies like round-robin, where requests are evenly distributed to each server in a cyclic manner.
Alternatively, a load balancer can use algorithms such as least connections or weighted round-robin to distribute requests based on the server's current workload or performance metrics. Load balancing can also be performed at different levels, such as DNS-based load balancing, where multiple IP addresses are associated with a single domain name. Overall, load balancing helps ensure high availability, scalability, and efficient utilization of resources in RESTful web services.
26. What is service discovery and how is it used in RESTful web services?
Service discovery is a mechanism used in RESTful web services to allow services to find and communicate with each other without manual configuration. It involves a central registry or service registry where services can register themselves and provide information about their location, endpoints, and capabilities.
When a service needs to communicate with another service, it can query the service registry to obtain the necessary information. This eliminates the need for hardcoding or manual configuration of endpoints, making the system more dynamic and flexible. Service discovery enables automatic load balancing, failover, and scaling in distributed systems, as services can easily discover and connect to available instances of other services.
27. Can you explain the concept of API gateway and how is it used in RESTful web services?
An API gateway is a server that acts as an entry point for requests to a RESTful web service. It provides a centralized point of control and helps manage the complexity of microservices architectures.
In this setup, the API gateway serves as a mediator between clients and services, handling authentication, authorization, traffic management, and other cross-cutting concerns. It allows clients to make requests to different services through a single endpoint, simplifying the client's access to various functionalities.
The API gateway also enforces security measures by, for example, validating API keys or implementing rate limiting. It can transform requests and responses, aggregate data from multiple services, and cache results to improve performance. Overall, the API gateway enhances the scalability, reliability, and security of RESTful web services.
28. What distinguishes a DELETE request from a HEAD request in REST API?
In a REST API, a DELETE request is used to request the deletion of a specific resource, identified by the requested URI[1]. This means that the resource should be removed from the server. However, it's important to note that the resource may not be removed immediately and the deletion could be an asynchronous or long-running process. The DELETE request is accompanied by status codes that indicate the result of the request, such as 2XX for success or 4XX for client errors.
On the other hand, a HEAD request is used to retrieve the metadata of a specific resource, such as the headers and other information, without getting the actual content of the resource. This is useful when the client only needs to check the availability or retrieve specific information about the resource, without the need to download the entire content. The server responds with the headers and status codes, but without the body of the resource.
29. What is the difference between API gateway and reverse proxy?
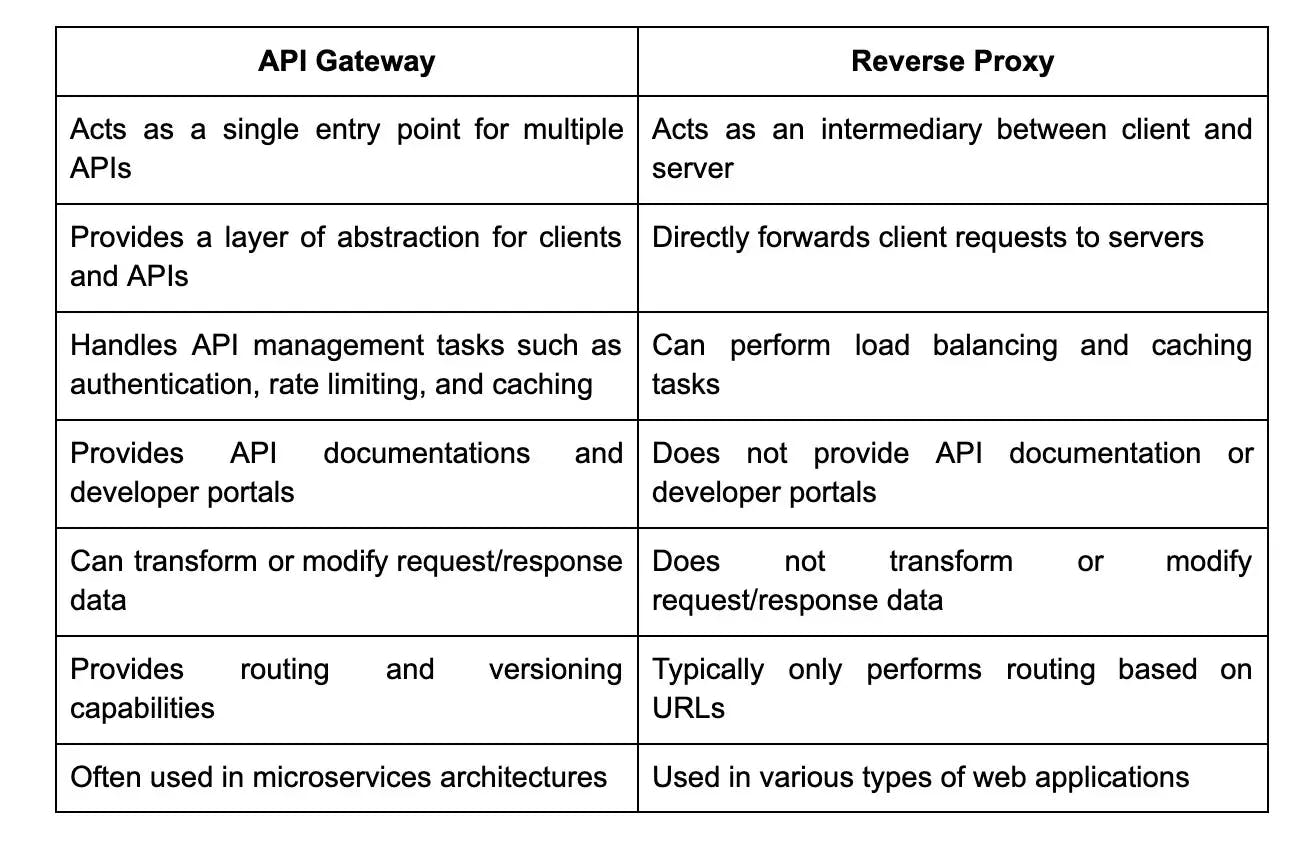
30. How do you implement token-based authentication in RESTful web services?
- User Authentication: When a user logs in or registers, their credentials (such as username and password) are validated against a user database. Once validated, a token is generated. This token can be a JSON Web Token (JWT) or any other form of secure token.
- Token Generation: The server generates a unique token that is associated with the user session or identity. This token contains information such as the user's ID and any necessary permissions or claims. It is digitally signed using a secret key known only to the server. The server then returns this token to the client.
- Client-Side Storage: The client (e.g., a web browser or mobile app) stores the token securely. This can be done using local storage, session storage, or even in memory for mobile apps. It is crucial to protect the token from unauthorized access. Storing the token securely helps prevent it from being stolen or tampered with.
- Token Submission: For every request that requires authentication, the client includes the token in the request header, typically as the Authorization header with the value "Bearer ". The server verifies the token's authenticity by checking its signature and expiration date. If the token is valid, the server allows the request to proceed.
- Authorization: Once the token is validated, the server performs any necessary authorization checks to ensure the user is authorized to access the requested resource. This can include checking permissions, roles, or any other relevant factors.
31. What is JWT and how is it used in RESTful web services?
JWT (JSON Web Token) is a standard format for tokens that are used to authenticate and authorize users within a web application. It consists of three parts: a header, a payload, and a signature. The header specifies the algorithm used to sign the token, the payload contains information about the user such as their ID and role, and the signature is used to verify the integrity of the token and ensure that it has not been tampered with.
In RESTful web services, JWTs are commonly used for authentication and authorization. When a user logs in to the web application, the server generates a JWT containing information about them, signs it with a secret key, and sends it back to the client. The client then includes this token in all subsequent requests to the server, allowing the server to verify that the user is authenticated and authorized to access the requested resources.
32. Can you explain the concept of OAuth and how is it used in RESTful web services?
- User initiates the process: When a user wants to connect their account on a service (known as the "resource server") to a third-party application (known as the "client"), they initiate the OAuth process by clicking on a "Connect with [client]" button.
- Authorization Request: The client redirects the user to the resource server's authorization endpoint along with information about the requested access and a redirect URL where the user will be sent after authorization.
- User gives consent: The user is presented with a consent screen by the resource server, which explains the requested access and asks for their permission to grant the client access to their resources.
- Authorization Grant: If the user consents, the resource server generates an authorization grant (e.g., an access token) and redirects the user back to the redirect URL provided by the client.
- Access Token Request: The client exchanges the authorization grant for an access token by making a request to the resource server's token endpoint, providing the grant, client credentials (e.g., client ID and client secret), and the redirect URL used in the authorization request.
- Access Token Issued: If the token request is valid, the resource server verifies the grant and returns an access token to the client.
- Accessing Protected Resources: The client can now use the access token to make requests to the resource server's API, including the user's protected resources. The resource server verifies the access token for every request, ensuring that the client has been authorized to access those resources.
33. What is CORS and how does it work?
CORS, or Cross-Origin Resource Sharing, is a security mechanism that allows web browsers to make requests to a different origin than the one from which the script was served. Browsers enforce the Same Origin Policy, which restricts requests to the same origin due to security concerns. CORS solves this issue by allowing server-side configuration to determine which origins are allowed and what types of requests are permitted.
When a browser makes a cross-origin request, it includes an "Origin" header with the requesting domain. The server then responds with appropriate headers specifying which origins are allowed and what actions are permitted. This helps prevent malicious scripts from accessing sensitive data from other origins.
34. What is the difference between a PUT and a PATCH request in REST API?
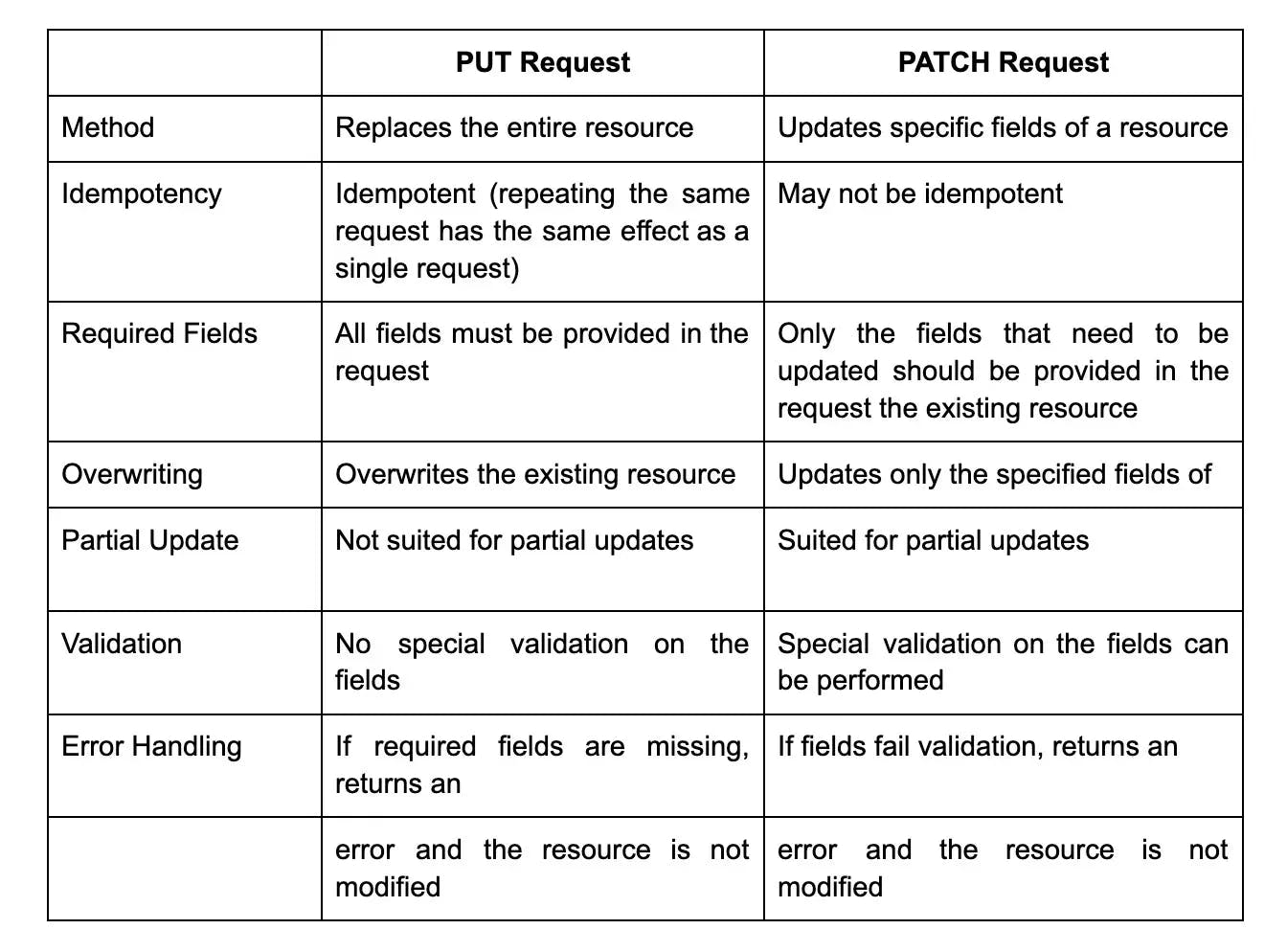
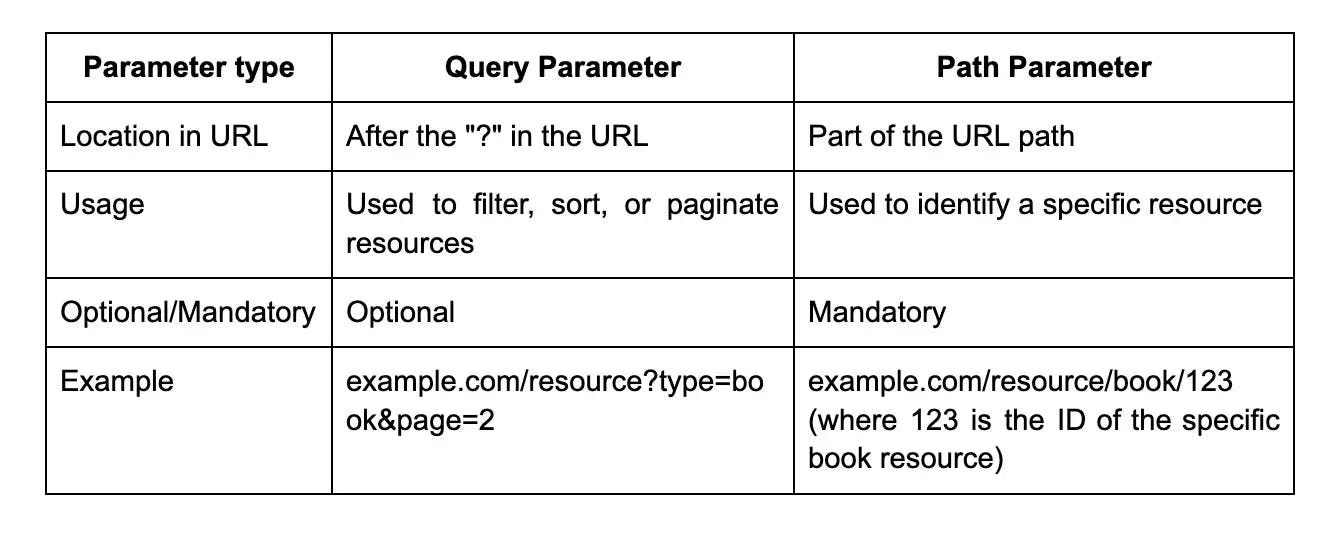
35. What is the difference between a query parameter and a path parameter in REST API?
36. How do you handle authentication and authorization in a REST API?
Authentication:
- Basic Authentication: The client includes the username and password in the request headers. This method is simple but not recommended for sensitive data as it transmits credentials in plaintext.
- Token-based Authentication: The server generates and returns a token (e.g., JSON Web Token or JWT) upon successful login. The client includes this token in subsequent requests to access protected resources.
- OAuth: A protocol that allows users to authorize third-party applications to access their resources without sharing credentials. It involves obtaining an access token from an authorization server and using it to make authenticated requests.
Authorization:
- Role-Based Access Control (RBAC): Assigning roles to users and defining permissions based on those roles. Users are authorized based on their assigned roles.
- Attribute-Based Access Control (ABAC): Defining policies that determine access based on attributes of the user, resource, and environment. It provides more granular control over permissions.
37. What is the difference between a GET and a POST request in REST API?
38. How do you handle errors in a REST API?
- Use appropriate HTTP status codes: Use HTTP status codes to indicate the result of the request. For example, use 200 for success, 400 for client errors (e.g., invalid input), 401 for unauthorized access, and 500 for server errors.
- Provide error messages: Include detailed error messages in the response to help clients understand what went wrong. It's beneficial to follow a consistent structure for error messages, including error codes and descriptive text.
- Include error details in the response body: In addition to the HTTP status code, include relevant error details in the response body. This can be done in a structured format like JSON or XML, providing information about the error cause and possible solutions.
- Use API versioning and deprecations: When making changes to an API, use versioning to support backward compatibility. If an endpoint is deprecated, clearly communicate this to the clients and provide alternative endpoints or migration instructions.
- Rate limiting and throttling: Implement rate limiting and throttling mechanisms to prevent abuse and ensure fair usage of the API. This can help protect the system from excessive requests and potential malicious activities.
- Log errors: Logging errors is essential for troubleshooting and monitoring the performance of an API. Log relevant information such as the error message, timestamp, request details, and any additional context that can assist in debugging.
- Custom error handling middleware: Implement custom error handlers or middleware to centralize error handling logic. This can help in consistent error formatting, logging, and handling of uncaught exceptions.
39. How do you version a REST API?
- Use URL Versioning: In this method, the version is included in the URL of the API endpoint. For example, you could have /api/v1/endpoint and /api/v2/endpoint for version 1 and version 2 of the API.
- Use Media Type Versioning: In this method, the version is included in the media type of the request and response. For example, you could have application/vnd.company.v1+json and application/vnd.company.v2+json for version 1 and version 2 of the API.
- Use Custom HTTP Headers: In this method, the version is included in custom HTTP headers. For example, you could use X-API-Version: 1 or X-API-Version: 2 for version 1 and version 2 of the API.
40. What are the benefits of using RESTful web services?
- Simplicity: REST is easy to understand and implement, as it utilizes the familiar HTTP verbs such as GET, POST, and PUT. With its simplicity, developers can quickly grasp the concepts and build RESTful APIs efficiently2.
- Compatibility: RESTful web services are built on top of HTTP, the widely understood and integrated protocol. This compatibility means that software, such as web browsers, can easily integrate and communicate with RESTful APIs without the need to understand complex protocols like SOAP.
- Scalability: RESTful web services can handle a high volume of requests and are highly scalable. This is due to the stateless nature of REST, where each request is independent and carries all the necessary information for the server to process it. This allows for easy load balancing and horizontal scaling of resources.
- Flexibility: RESTful web services can support a variety of data formats, including XML and JSON. This flexibility enables developers to choose the most suitable format for their application's needs. JSON, in particular, is lightweight and offers faster parsing, making it commonly used in RESTful APIs.
41. How do you ensure the security of a REST API?
- Authentication and Authorization: Use strong authentication mechanisms like OAuth or JWT to verify the identity of the clients and provide access only to authorized users.
- Transport Layer Security: Implement SSL/TLS to encrypt the data transmitted over the network and prevent eavesdropping or tampering.
- Input Validation: Validate and sanitize all input data to prevent injection attacks like SQL or XSS.
- Rate Limiting: Implement rate limiting to prevent unauthorized access or abuse of the API.
- Security Testing: Regularly perform security testing, such as penetration testing, to identify vulnerabilities and fix them promptly.
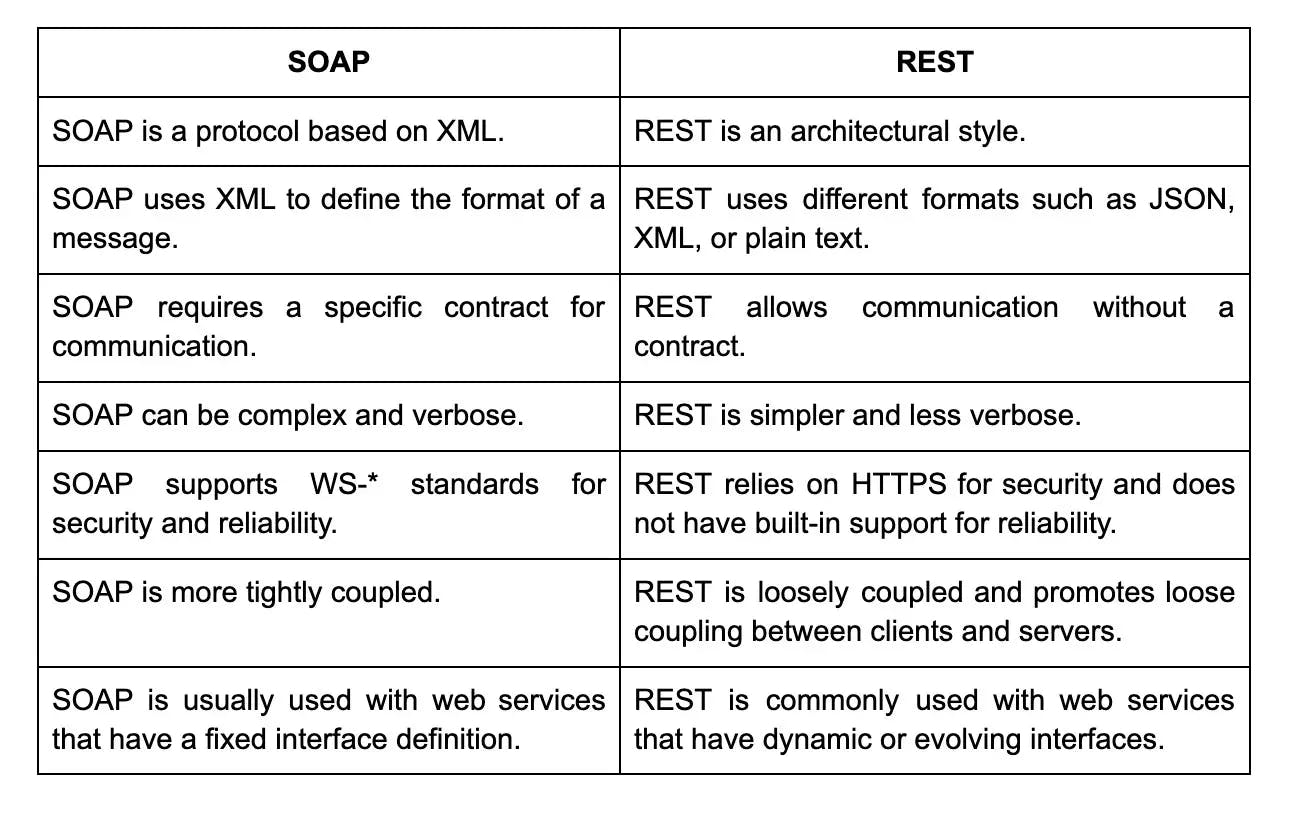
42. What is the difference between SOAP and REST?
43. How does the use of HTTP status codes differ between a successful and failed request in REST API?

44. How do you handle pagination in a REST API?
In a REST API, pagination is often used to limit the amount of data returned in a single request. There are different approaches to handling pagination. One common approach is to use query parameters, such as "page" and "limit", to specify the desired page number and the number of items per page. The API can then use this information to retrieve and return the appropriate data subset. Alternatively, the API can return a next page token or link in the response, allowing the client to request the next set of data. Pagination is important for improving performance and ensuring that large data sets are processed efficiently.
45. What is HATEOAS and why is it important in REST API?
- HATEOAS stands for Hypermedia as the Engine of Application State. It is a principle in RESTful APIs that allows clients to navigate through available resources by following hypermedia links returned in the API response. This means that instead of the client needing prior knowledge of resource URIs, the server provides information about related resources and actions that can be performed.
- HATEOAS is important in REST API because it enables a self-descriptive API. Clients can discover and interact with resources dynamically, reducing coupling between the client and server. This makes the API more flexible and allows for easier evolution and scalability. HATEOAS also promotes code readability and improves the overall usability of the API.
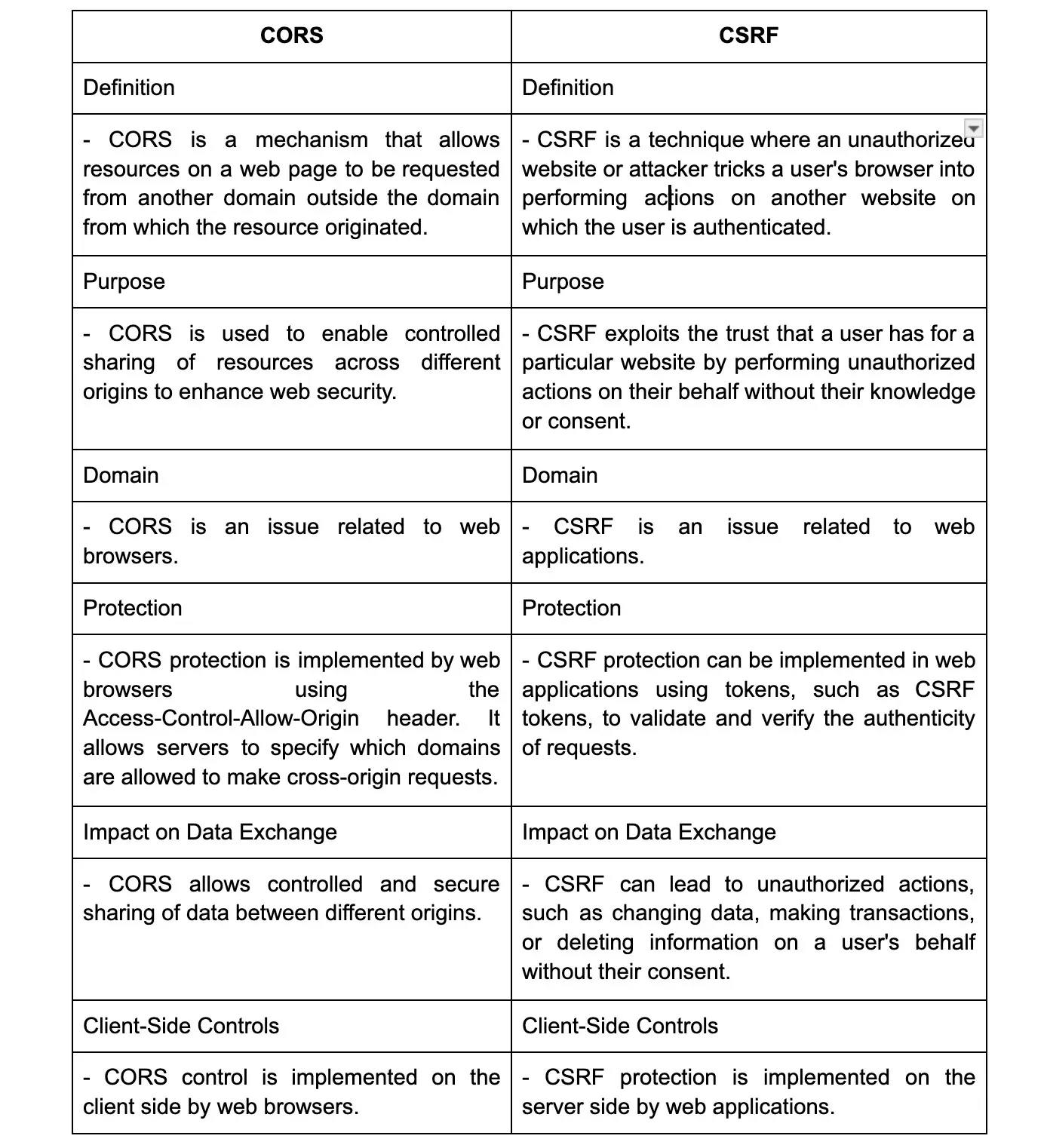
46. Can you explain the difference between CORS and CSRF?
47. How does REST API work?
REST APIs work by using HTTP methods (such as GET, POST, PUT, and DELETE) to perform different operations on the resources exposed by the API. The API follows a client-server architecture where the client sends a request to the server, and the server responds with the requested data or performs the requested action. The communication is stateless, meaning that each request is independent and does not rely on previous requests. REST APIs commonly use JSON or XML format to exchange data between the client and server.
48. Can you explain the difference between REST and SOAP?
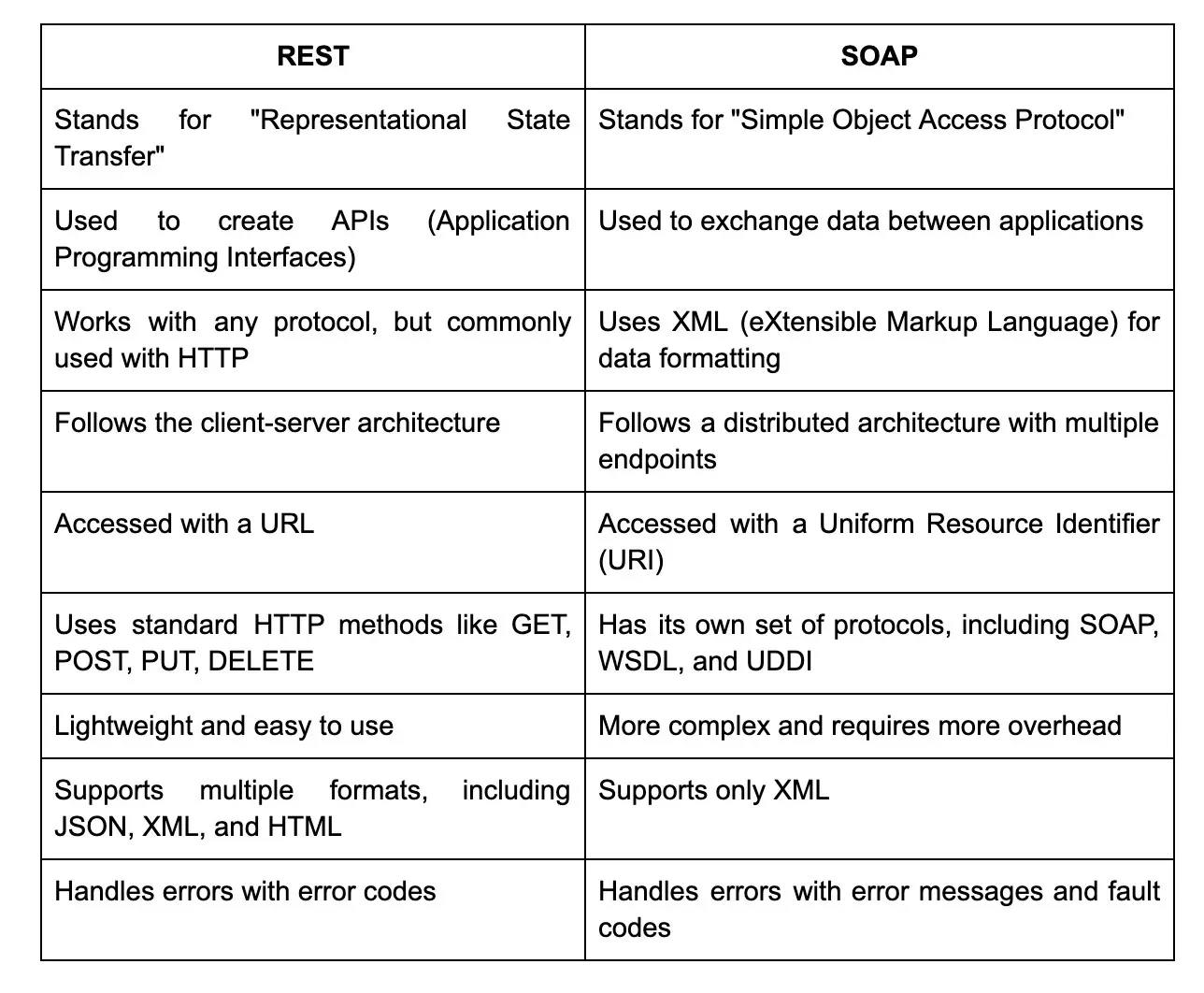
49. What are the key features of RESTful web services?
The key features of RESTful web services include statelessness, which means that each request from the client to the server must contain all the necessary information for the server to understand and process it. This allows for scalability and reliability.
Another feature is the use of HTTP methods such as GET, POST, PUT, and DELETE to perform different operations on the resources. RESTful web services also emphasize the use of URIs (Uniform Resource Identifiers) to uniquely identify and access resources.
Additionally, RESTful web services often return responses in a lightweight format such as JSON or XML, making them easily consumable by clients.
50. How do you design a RESTful API?
To design a RESTful API, there are several key principles to consider. First, the API should be stateless, meaning each request contains all the information needed to understand and fulfill it.
Next, the API should use standard HTTP methods (GET, POST, PUT, DELETE) to perform operations on resources. It should also follow a consistent naming convention for endpoints that are descriptive and easily understood.
Additionally, the API should support versioning to allow for future changes without breaking existing clients. It is also important to use appropriate status codes and error handling mechanisms to provide clear feedback to clients.
Finally, consider implementing authentication and authorization mechanisms to ensure security.
51. Can you explain the HTTP methods used in RESTful web services?
- GET: Used to retrieve a resource or a collection of resources.
- POST: Used to create a new resource.
- PUT: Used to update or replace an existing resource.
- DELETE: Used to remove a resource.
52. What is the difference between the GET and POST methods?
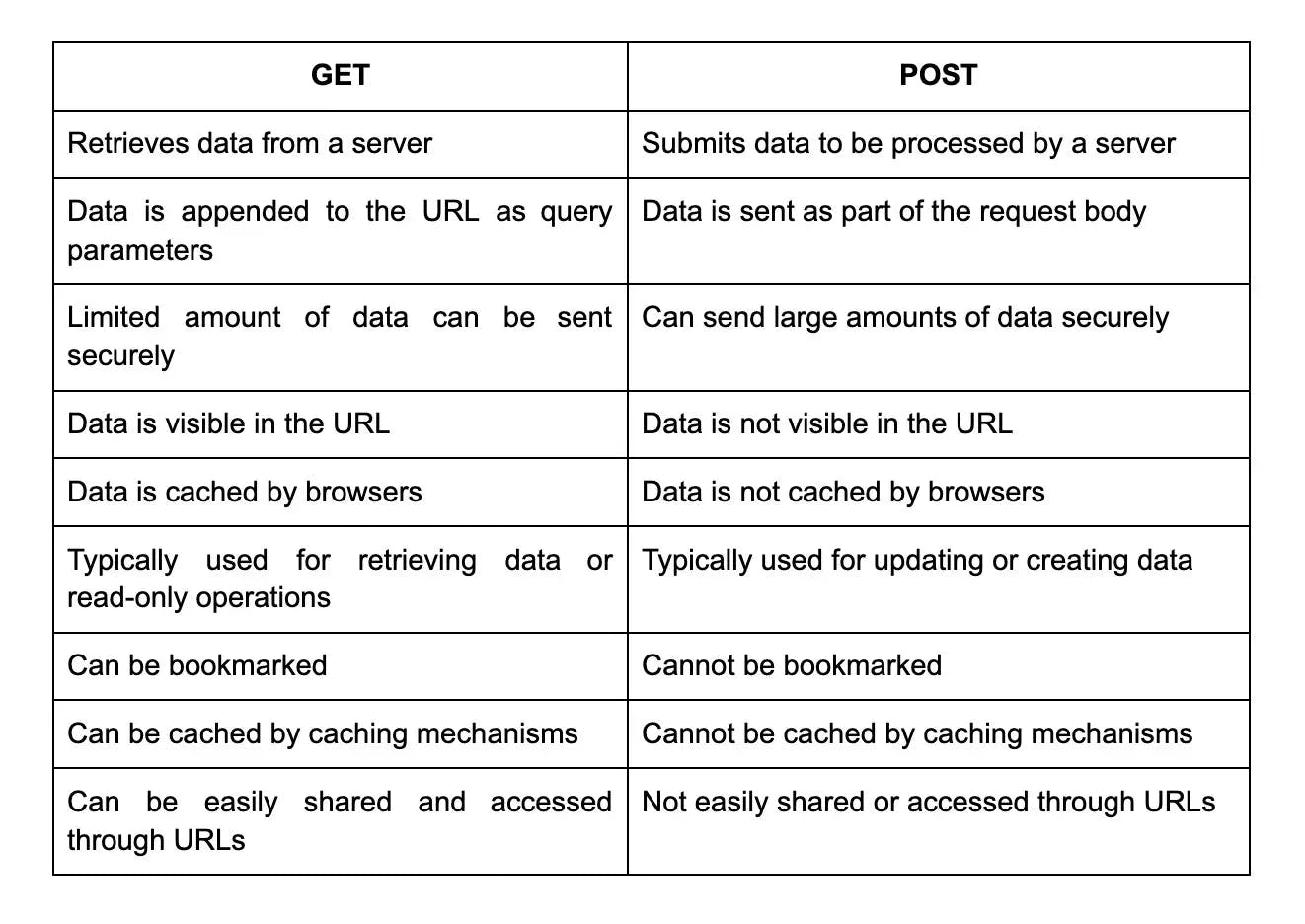
53. What is the difference between the PUT and PATCH methods?
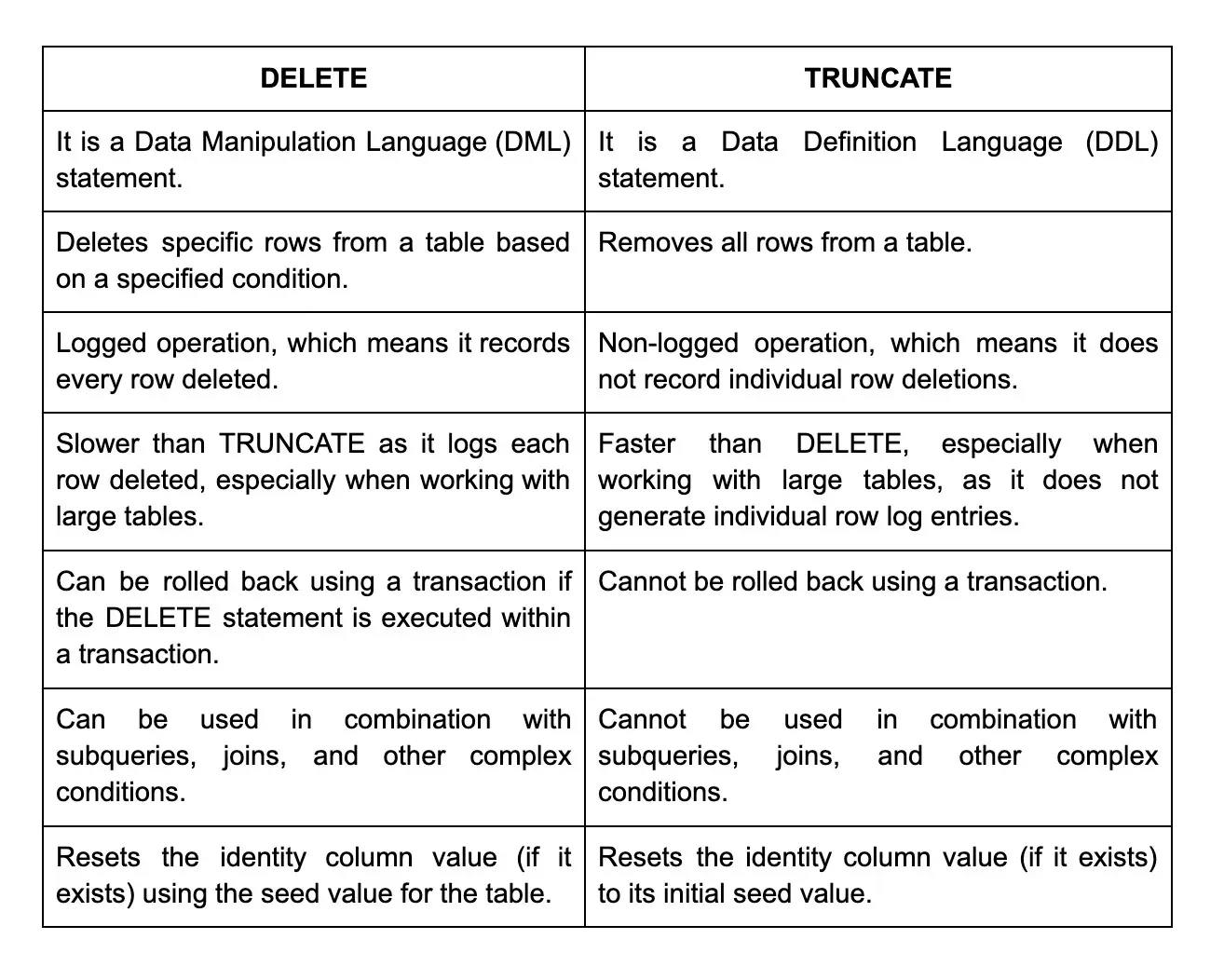
54. What is the difference between DELETE and TRUNCATE methods?
Wrapping up
In conclusion, this blog has provided a comprehensive list of the top 100 REST API interview questions, catering to a wide range of audiences - from Java developers to experienced API professionals. However, the journey does not end here. If you're an employer seeking exceptional developers or an experienced professional ready to advance in your career, Turing can help facilitate that journey. Turing believes in creating connections, promoting growth, and propelling the world of technology forward. By joining Turing, you open yourself to exciting opportunities in the realm of REST API and beyond, unlocking your full potential. Don't miss out - join Turing today and take the next step in your REST API career.
Hire Silicon Valley-caliber REST/RESTful APIs developers at half the cost
Turing helps companies match with top quality remote JavaScript developers from across the world in a matter of days. Scale your engineering team with pre-vetted JavaScript developers at the push of a buttton.
Tired of interviewing candidates to find the best developers?
Hire top vetted developers within 4 days.
Leading enterprises, startups, and more have trusted Turing

Check out more interview questions
Hire remote developers
Tell us the skills you need and we'll find the best developer for you in days, not weeks.